Way back in March, 2019 Security Discovery’s Bob Diachenko discovered a non-password protected database that contained 18,000 user names, mailing addresses, hashed passwords, and credit card information such as the last 4 digits of the card, and the expiration date. Upon further investigation we were able to verify the source, and owner of this information with Wyatt Research, based out of Richmond, Vermont. The database also contained evidence of ransomware demanding 0.o5 Bitcoin or $500. The most shocking part was that Wyatt Investment Research’s database was open to anyone with an internet connection from at least early March to July 22nd.
Wyatt Research produces Independent Investment Newsletters under a number of different Publications including, Personal Wealth Advisor, High Yield Wealth, Million Dollar Portfolio, High Yield Trader, Dividend Confidential, Options Advantage, Millionaire’s Retirement Club. According to their website, Wyatt “…offers independent investment research and analysis of the financial markets, stocks, bonds, ETFs and mutual funds to nearly 250,000 individual investors every day.”
As many advisors inform their customers of the importance of reducing market risk through proper asset allocation, we recommend that companies reduce the threat of a cyber security incident through the implementation of a diligent Data Security Policies. This includes having a response plan in place for when a member of the security community reaches out with a data incident notification.
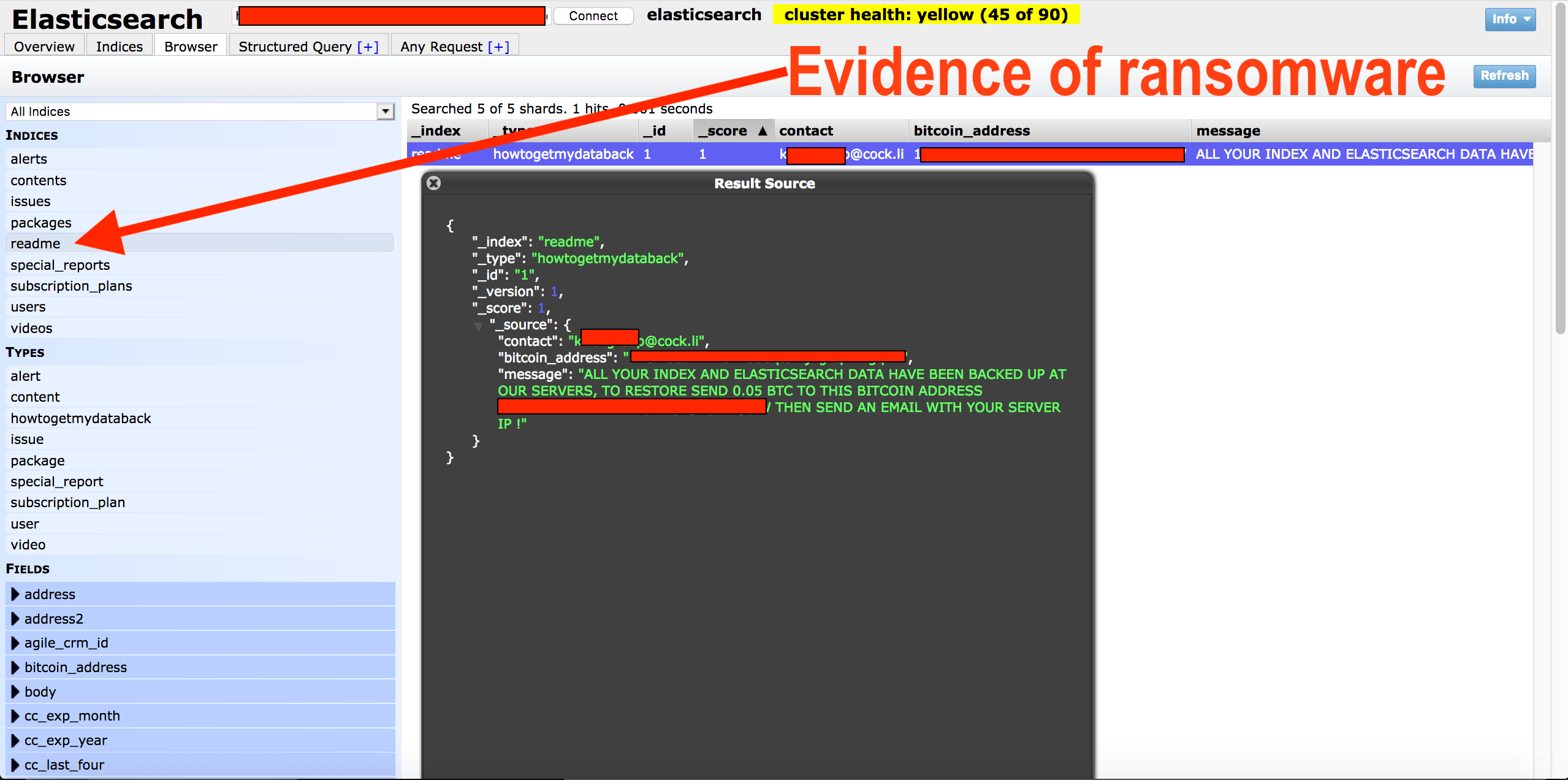
Here is what we discovered:
This is an Elastic database set to open and visible in any browser (publicly accessible) and anyone could edit, download, or even delete data without administrative credentials.
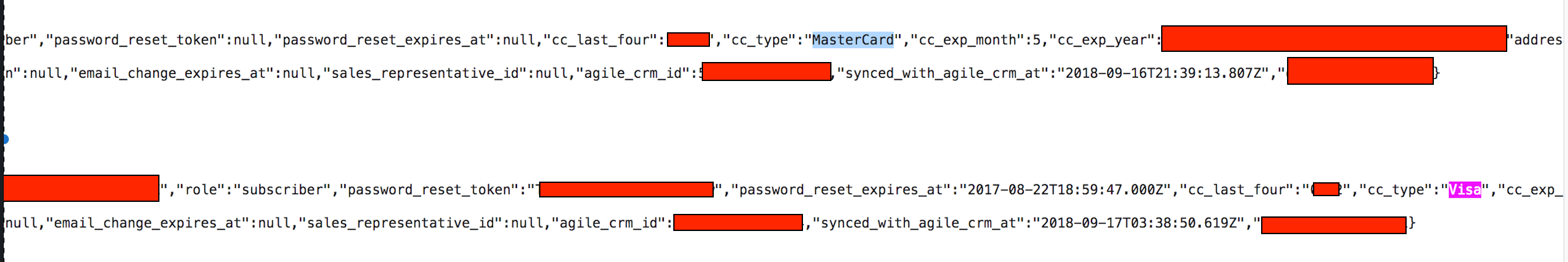
22,396 records including 18,300 customer accounts containing names, addresses, email, hashed passwords and partial Credit Card numbers in plain text.
IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper into the network.
Evidence of Ransomware inside the network.
On July 22th I spoke with a member of Wyatt Research’s management team to discuss the incident, and the nature of our findings. We sent the same email notification which thoroughly outlined our findings, and the severity of the information that was exposed. We received an email on August 9th that they had “not heard back yet from their tech team yet”.
This is yet another wake up call that organizations must do more to protect the data they collect and store and if that sensitive data is publicly exposed they have an obligation to notify their customers. At the time of publication I could not find any mention of Wyatt Research notifying clients or subscribers that their data was exposed.
It is unclear if the affected customers or the authorities were notified of this exposure that included financial data in the form of partial credit card numbers. As part of our responsible disclosure process we do not publicly disclose the discovery until companies or organizations complete their internal investigation. Throughout the process we are happy to share details of how the discovery was identified or other important information. In this instance there was more than adequate time for any internal processes.
Under Vermont law personal information such as Social Security Numbers, credit and debit card numbers, and bank account information must be kept confidential and secure. Businesses are required to notify the Office of the Attorney General within 14 days of discovering or being notified of a breach. The notification to consumers must be sent as soon as possible and without unreasonable delay, and no later than 45 days after discovery or notice of the breach. Depending on the size of the breach, the notice must be individual in a specific form or through mass media.
We are grateful to have played a role in the protection of sensitive public information. We hope that companies can take these instances to implement, or improve their Data Security Policies, and build awareness through ongoing due diligence.