Two words no one wants to hear are “data breach”. It can not only be a nightmare for your reputation but could also result in fines or legal trouble. So the reality is no one is ever ready for a data leak or data breach, so when it happens it can have a devastating effect on your operations. Prevention is of course the best option, but what to do after a data breach is often more important.
 We would recommend that you have a plan in place to review your endpoint protection, data backup and recovery strategy. The data leak could wipe you out if your database was hit by ransomware for example. This is why you have to have a plan to get back up and running once an attack has been resolved or what to do after a data breach. Unfortunately, there’s no single plan of action for a data breach.
We would recommend that you have a plan in place to review your endpoint protection, data backup and recovery strategy. The data leak could wipe you out if your database was hit by ransomware for example. This is why you have to have a plan to get back up and running once an attack has been resolved or what to do after a data breach. Unfortunately, there’s no single plan of action for a data breach.
These simple steps outline the basics of what you shouldn’t do if you realize your data infrastructure has been breached. The more you understand about a data breach the better in the long run and the faster you can get back to work with better data protection. Here is some advice of what to do after a data breach.
1. Have a plan and never make it up as you go
In the event of a data breach or a cyber attack you need to act fast and gather the facts of what happened and why. Here is where not having a plan or a strategy can clearly hurt you because any bad decisions you make after an attack could worsen the situation. You should make someone in your responsible for decisions to lead the recovery plan. If you do not have a plan you should reach out to an expert, consultant, or agency with experience in creating an incident response plan.
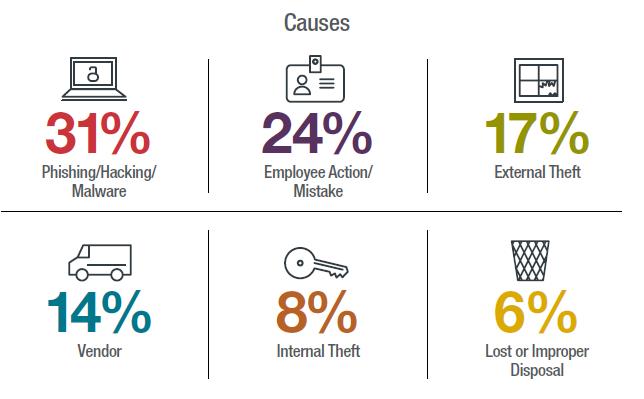
Although most companies think of their reputation and lost revenue first, it is important to remember the customers or partners who’s data you are entrusted with protecting. Next you must identify how the data breach happened. Was this a ransomware attack, malware on the system, a firewall with an open port, outdated software, or unintentional insider threat?
Getting help from an experienced third-party expert will help handle and mitigate the impact of damages. Every step, action, or statement after a data breach can have a long lasting effect. Depending on the size of your business you may even need public relations and communication experts to help you plan your messaging or statements.
2. Never Ignore a Data Breach
A Security Breach will not go away if you simply don’t reply to inquiries from researchers, journalists, or even worse cyber criminals. Proper disclosure is important when forensic analysis shows that multiple people outside of your origination accessed your data. We recommend that you notify employees, partners, and customers if their data has been exposed by a data breach. Be honest, open, and transparent and explain how it happened and what you will do to remedy the situation.
Employees or customers should never learn from the media that your origination had a data leak. Telling employees can make sure that there is a messaging plan and that they can not talk to media or say something that they are not authorized to talk about. A professional agency or consultant can provide you with an incident response plan if you need help, but you can not remain silent and hope that it all goes away.
3. Don’t Lie or Make Things Up : Facts Only
This seems like pure common sense to not be anything except honest with your employees, partners, media, or customers, right? When we first started doing security research several years ago we found an application that dealt with children’s data. When we reported the fact that the organization has left their database publicly accessible instead of simply saying “yes, sorry we made a mistake thanks for letting us know” the owner made wild claims to the journalist we were working with. He claimed that not only had we hacked his database but had also stolen access and spent money from accounts inside. This was not just any reporter or neighborhood newspaper, this was the BBC.
With such sensational claims against the researchers who notified him of the open port a small story about a unfortunate data breach became a giant story and followup. By making things up the owner of the origination came out looking foolish, impulsive, dishonest, misleading and the list goes on and on. You get the idea, but the main point is be honest and never attack the messenger who brings you the bad news. There have been many other cases where it was human error that exposed their data and the company tried to spin some wild fantasy in an attempt to not accept blame or responsibility.
4. Investigate, Find Out What Happened and Why?
Understanding what happened is key to preventing the next intrusion or data leak. You have to have a clear picture of what systems and data were impacted and then after the data breach how did your team address or resolve the problems? Having a final review is important because you can learn what you did right, what you did wrong, and everything in-between. If you are like most companies focusing on business is your primary goal and not doing research or data security. This is why you might want to hire an external team to conduct this investigation for you
any messaging, and craft your response plan. Data breaches happen but what to do after a data leak can make the difference.
After the data breach you must identify any gaps in your security strategy and an aggressive approach to proactive data protection. If you need help with what to do after a data breach contact us and we can help you.

