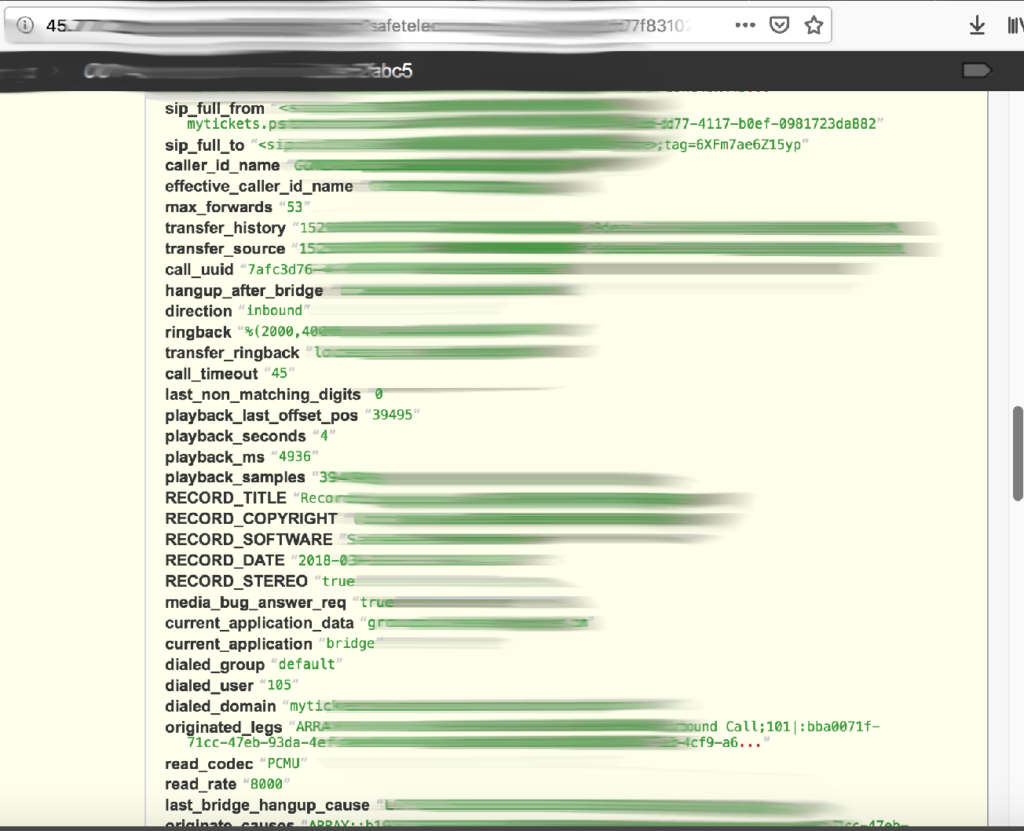
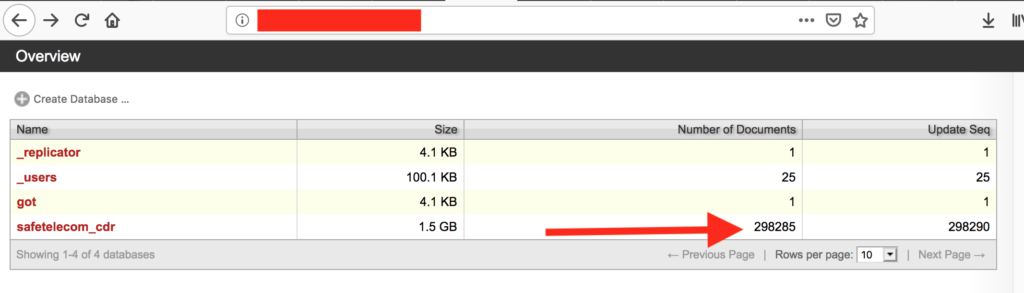
VOIP is Voice over Internet Protocol and just as the name suggests it allows for the delivery of voice communications and multimedia over the internet. As a security researcher I find lots of interesting things hidden away on the internet. I have seen everything from secret recipes of a Chinese restaurant to thousands of credit cards in plain text. However, one new trend I have discovered is internet based telephone service databases with thousands of recordings. The strange thing is that they do not seem to be connected to each other and it is really difficult to discover who they belong to. I have sent multiple notifications to any email or domains I find and yet they are all still alive and active.
The Danger of a VoIP Hack
VoIP attacks are nothing new and on the rise according many in the security community. The real danger of exposing your VoIP credentials is that most likely the network uses the same pathway for internet traffic. This could potentially allow cyber criminals to use your VoIP connection to exploit your network and get much deeper in your infrastructure. This simple phone connection could be a huge vulnerability. When all of this information is exposed it would be very easy for cyber criminals to steal business data, financial information, listen to conversations or recordings, and even use your credentials to make calls that will appear to come from your organization. Toll fraud is where criminals access your VoIP network and route calls through your server with no hacking involved.
“I listed to hours of voicemails, small business sales people, doctor’s offices, telemarketing, real estate agents and more. Some even gave personal information and although you have to dig deep there is sensitive data hidden in nearly every database” – Jeremiah Fowler, Security Discovery Researcher
Be Proactive and Protect Your Network
There is no single method of communication that is completely safe and private. Many companies chose VoIP because is is cheaper than a traditional landline phone system, calls can be recorded, and many other features such as predictive calling or the beloved “auto dialers” are included with software or 3rd party applications. If your company or client uses VoIP it should be routinely tested for public access when you are conducting security audits on your infrastructure.
One easy fix is to require IP authentication for outbound calls from your network.The will prevent anyone outside of your authorized network from making calls or sending messages from your VoIP server. There are plenty of third-party tools that allow restrictions, create of an IP blacklist, limit login attempts and more. The most important thing to remember is to not sit around and wait for a data breach or malicious attack. Companies big and small have to remain proactive and vigilant against cyber threats and this includes your phone network.
I can not determine why so many VoIP databases are exposed or why no one replies to the breach notifications, but companies who record all calls also need storage for thousands and thousands of large audio files. If those databases are left unsecured and open to the public it is like leaving the front door of your network open.