Elasticsearch misconfigurations and related data incidents have became top news recently, even after Elastic introduced free security packs for all their users. Nevertheless, we at SecurityDiscovery.com, are still registering 5-10 big cases every month and this number does not seem to be decreasing.
On May 28th, I discovered an open and publicly available Elasticsearch instance with data that appeared to be part of The University of Chicago Medicine. This was a huge database with what appeared to be a collection of ‘leads’ and ‘perspective and existing givers’ for the organization.
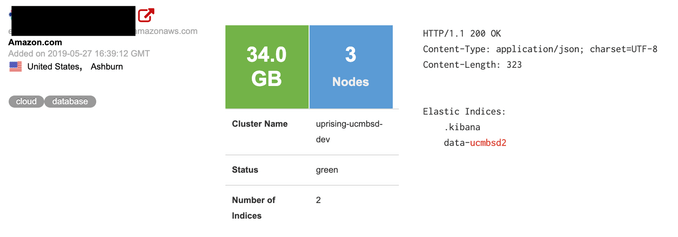
A 34GB-sized cluster named ‘data-ucmbsd2‘ was indexed by the Shodan search engine and could have been accessed by anybody who knew where to look.
The database contained 1,679,993 records with a various information such as:
- Full name
- DOB
- Full address
- Phone number(s)
- Emails
- Gender
- Marital status
- Wealth info and current status
- Communication notes etc.
After further investigation I was able to discover the identification of the alleged owner and sent a notification to the University of Chicago Medicine. After my notification the database was secured within 48 hours. The organization provided me with the following statement:
“Thank you for bringing this to our attention in a way that allowed us to secure the affected database, prevent unauthorized use or disclosure, and protect our systems and information. As we learn more from our ongoing investigation, we will comply with our responsibilities under all applicable laws and regulations”
The danger of having an exposed (passwordless) Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the ES servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
***
As we see a never-ending loop of these incidents, we at SecurityDiscovery.com have decided to offer a live educational session (webinar or offline workshop) for raising cyber security awareness within your organization, to prevent potential issues in the future. We use real world examples and promote that data security is important to every employee and at every level inside the organization.
It can be an online webinar session (estimated 1h long), with Q&A session or an offline meeting in your offices, live interaction with your team (master class included).
Proposed content includes
- Description of tools and techniques we use to identify vulnerabilities, PII and sensitive data online: no hacking, just google-it.
- How to ensure your data / your company’s data is not exposed to the public internet, security tips from professionals
- Recommendations and best practice on main noSQL databases configurations and maintenance (MongoDB, CouchDB, Elasticsearch)
- Case studies: analyzing related data appearance online
- Live search for data and master class (for Option 2 only)
Please feel free to send your requests to alert(at)securitydiscovery.com or bob(at)securitydiscovery.com
Let’s educate your team!