On August 4th I discovered an open and unprotected MongoDB database which appeared to be part of a Spanish company managing a chain of “men’s clubs” across the country.
IP with the database in question was found via BinaryEdge. This platform is a really great search engine with a team of dedicated professionals behind the wheel and I highly recommend anyone to use it to make sure that your digital assets are not exposed to the public.
The following collections were part of the database and contained extremely sensitive information, such as:
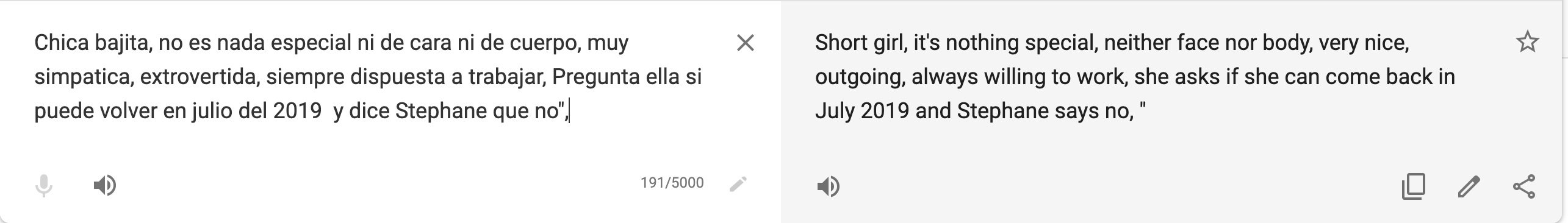
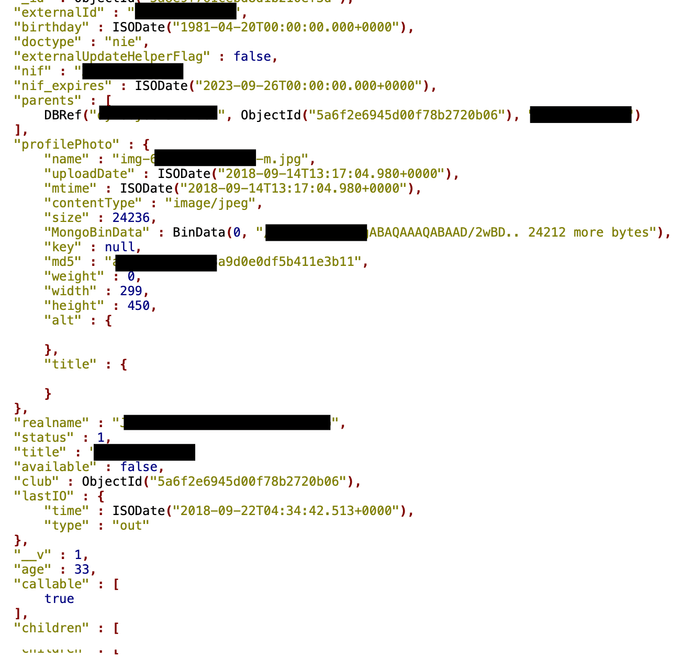
- 3,350 girls full profiles, with real names, DOBs, nationality, scanned IDs (stored as base64 output right in the database) and internal comments left by management, e.g.:
- 4,636 customers comments, with IP, email, name, coordinates and user device characteristics.
- Clubs turnover stats
- Internal configuration details (encrypted admin passwords and logins)
- And many more.
Upon further research on the sensitivity of the issue, I decided to get in touch directly with data owners using emails indicated in the database listed as administrators. It was important to responsibly disclose this incident, as many people’s sensitive information was at obvious risk.
According to Tripsavvy.com, despite some sources claiming that prostitution is legal in Spain, the truth is that sex workers exist in a legal vacuum wherein the practice has been decriminalized since 1995 but no public laws have been written regarding the legal status of sex workers.
The workers themselves are not penalized, but instead, the procurers are the ones who are punished by the law. According to a 2009 study by TAMPEP (European Network for HIV/STI Prevention and Health Promotion among Migrant Sex Workers), 90 percent of sex workers in Spain are said to be victims of human trafficking, which violates international law.
Brothels have been illegal in Spain since 1956, but these days, the vast majority of them are loosely disguised as whiskerías or “clubs” and are left to function as normal.
On August 6th, I sent a notification and on the same day I got a response from the alleged owner of the data who thanked me for the alert and shut down the access to the exposed instance.
I have purposely left this post without any attribution to the company responsible for the misconfiguration. My only goal is to focus not on the nature of the exposed data but the cyber hygiene in general and again highlight the importance of keeping sensitive data secured – especially those that might be easily manipulated if/when exposed.
The danger of having an exposed MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
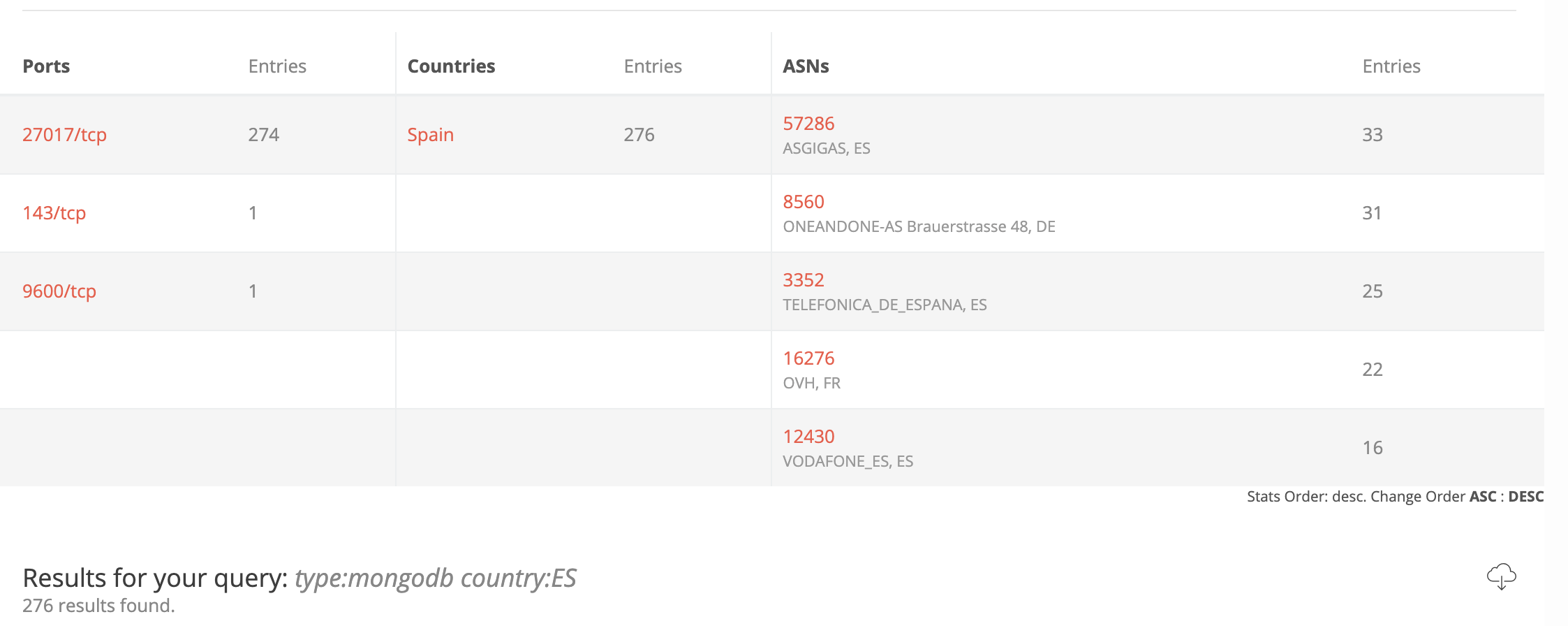
Currently, there are 276 open and exposed MongoDBs listed in Spain, as per BinaryEdge estimation: