PrankDial lets you:
- Choose from hundreds of prank call scenarios
- Send 3 prank calls for free
- Listen to their reactions afterwards (they are recorded)
- Users get a call history of all their reactions
- Users can submit their reactions so other people can rate/comment on them.
- Users get three free calls a day, if you want to send more calls, you can earn or buy tokens.
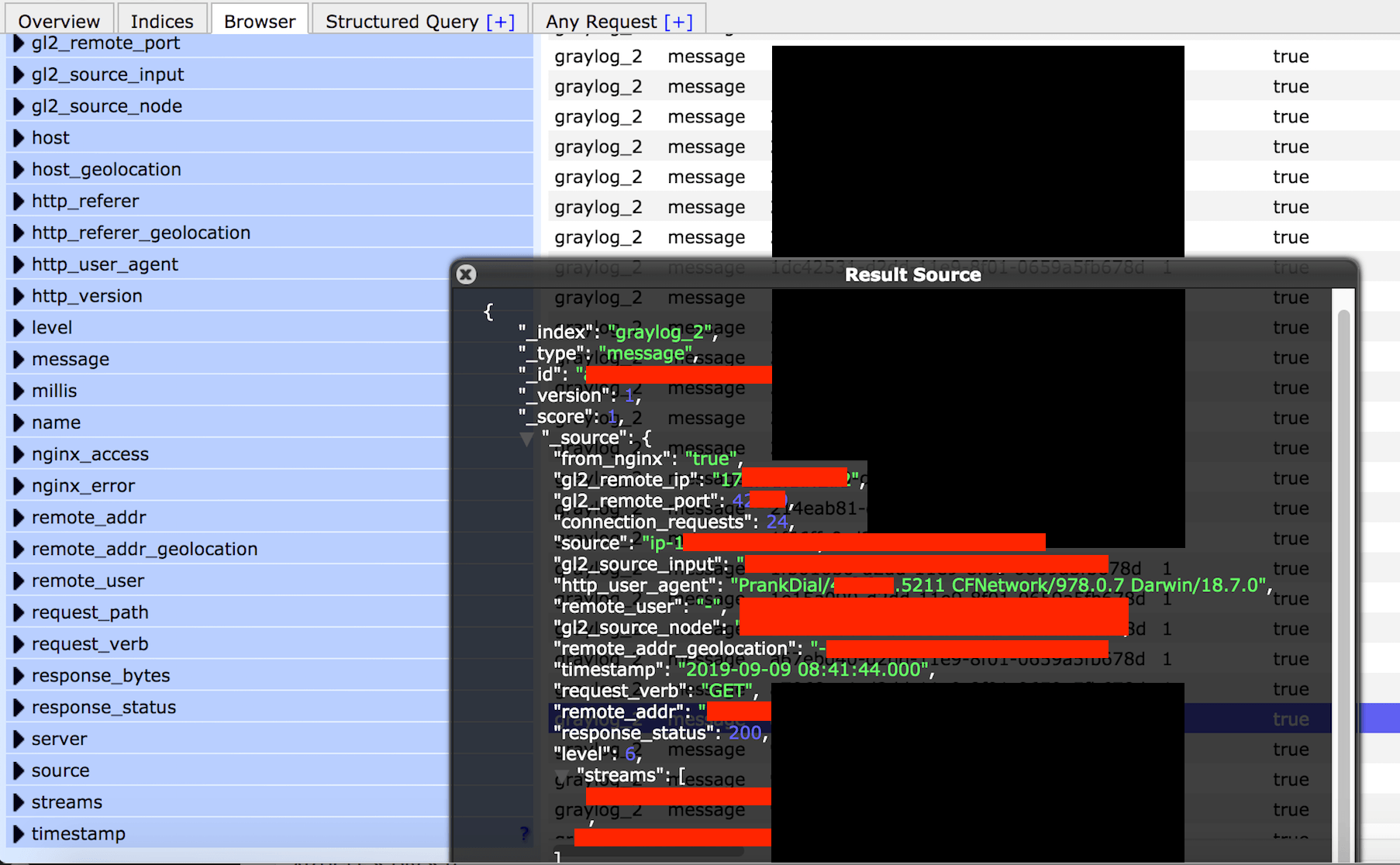
What the database contained:
- 138 Million log records in total.
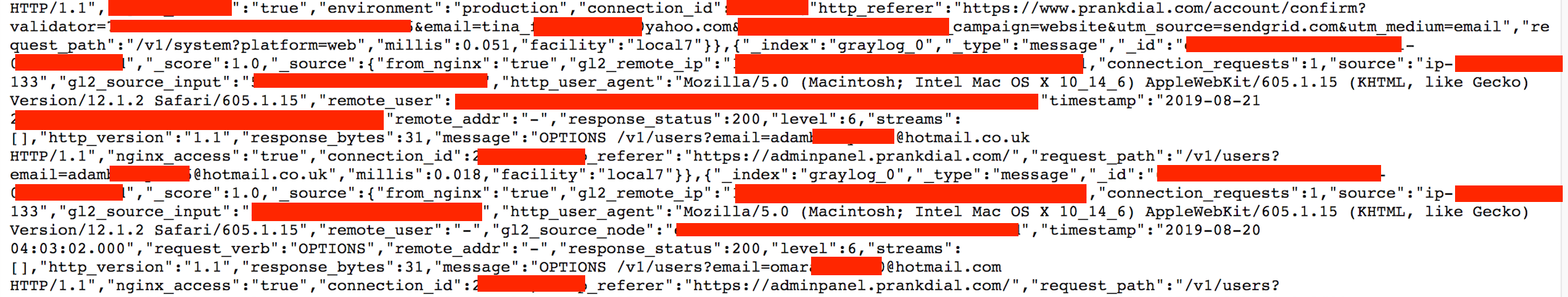
- User emails, credentials and password reset tokens, user IP addresses exposed in the logs.
- Device, operating system and version info.
- Internal IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper in to the network.
I sent multiple requests to KickBack Apps and PrankDial but no one every replied or acknowledged my discovery, instead they simply closed public access to the logs. It should be noted that I did not see phone numbers. I can only assume that the numbers are routed through a VOIP server and did not appear to be part of this dataset. At the time of publication no statement has been given by KickBack Apps / PrankDial and I will update the article in the event we are provided any statement or more details.