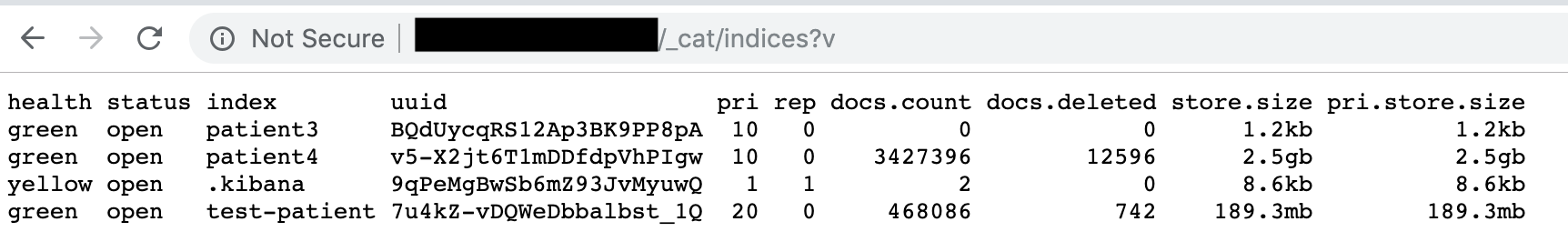
On May 10th I identified a massive bulk of data sitting in an unprotected and publicly available Elasticsearch cluster (hence visible in any browser).
This database contained 3,427,396 records with detailed information on Panamanian citizens (labeled as ‘patients‘), plus 468,086 records with records labeled as ‘test-patient‘ (although, this data also appeared to be valid and not purely test data).
Each record contained the following info:
- full name
- date of birth
- national ID number (cedula)
- medical insurance number
- phone
- address
- other info
With Panama’s total population number at 4,1M, the exposed number of 3,4-4,8M records would correspond to almost 90% of the country’s citizens.
I have immediately sent a notification alert to CERT Panama, and within 48 hours the database has been secured.
According to Shodan historical data, the IP in question has been indexed since April 24th, 2019 and it is unknown whether anyone else has accessed the data.
The danger of having an exposed Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.