On September 9th, I have discovered three (3) open and unprotected MongoDB instances which appeared to be part of Librería Porrúa, a long-established bookseller based in Mexico.
This case would have been left unnoticed if I did not report the same database caught exposed back in July this year.
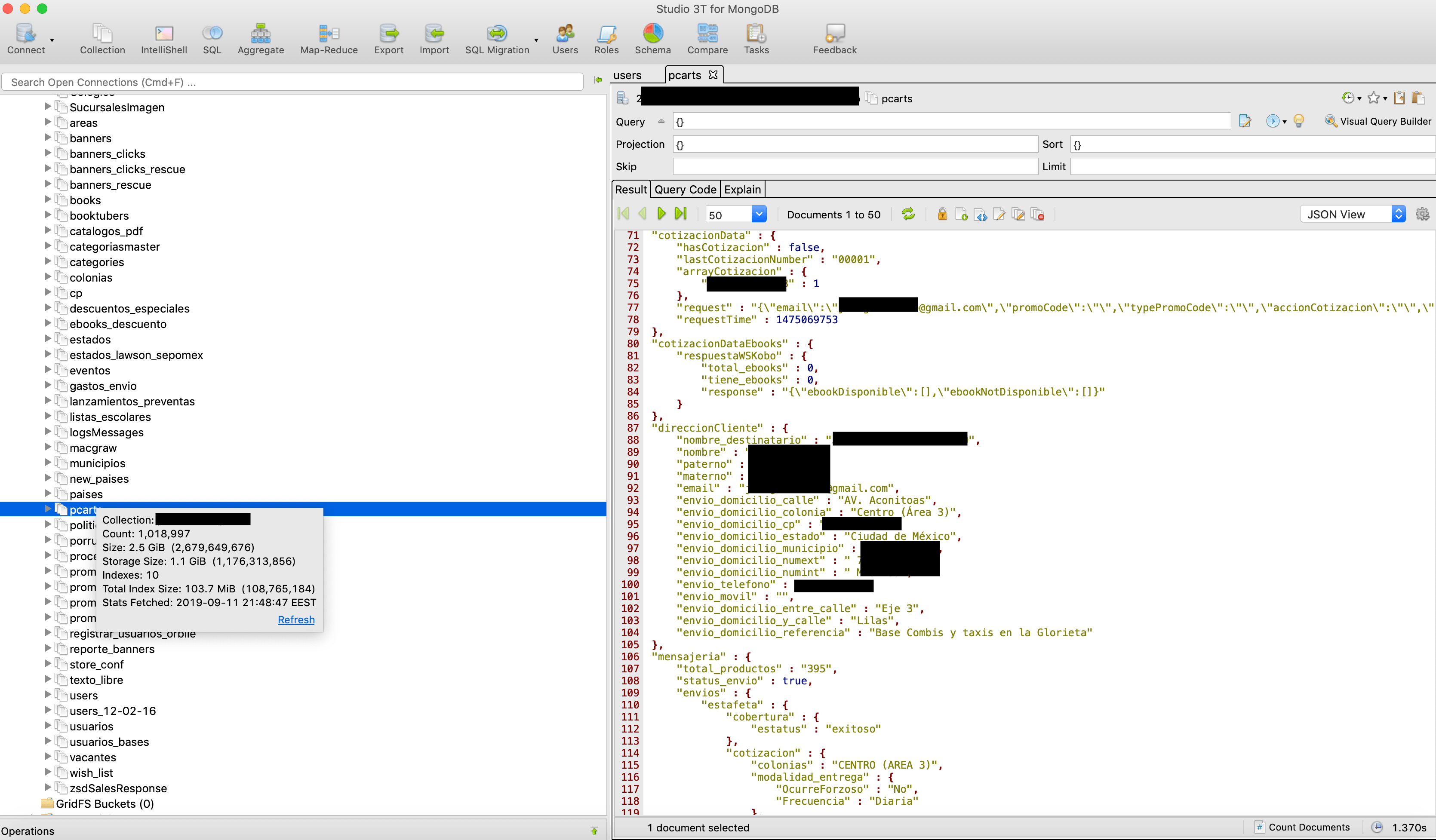
New version of the database contained even more records = 1,018,997 (comparing to the same collection with 958,128 records last time), meaning that this production database has been updated since the previous exposure with 60,869 new users.
Similarly to the previous incident, the following information was compromised:
- full name
- address
- phone number
- authorization tokens
Interestingly, both databases contained the same ransom note which has been seen in the previous incident – asking for 0.05 BTC. This could mean that developers simply migrated the same database to the production servers without cleaning up unnecessary stuff.
I have immediately sent a responsible disclosure note to Librería Porrúa and, surprisingly, on the next day (Sept 12) I heard back from IT manager who secured the database within 24 hours.
Danger of having exposed MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
***
As we see a never-ending loop of these incidents, we at SecurityDiscovery.com have decided to offer a live educational session (webinar or offline workshop) for raising cyber security awareness within your organization, to prevent potential issues in the future. We use real world examples and promote that data security is important to every employee and at every level inside the organization.
It can be an online webinar session (estimated 1h long), with Q&A session or an offline meeting in your offices, live interaction with your team (master class included).
Proposed content includes:
- Description of tools and techniques we use to identify vulnerabilities, PII and sensitive data online: no hacking, just google-it.
- How to ensure your data / your company’s data is not exposed to the public internet, security tips from professionals
- Recommendations and best practice on main noSQL databases configurations and maintenance (MongoDB, CouchDB, Elasticsearch)
- Case studies: analyzing related data appearance online
- Live search for data and master class
Please feel free to send your requests to alert(at)securitydiscovery.com or bob(at)securitydiscovery.com
Let’s educate your team!