In another MongoDB-related misconfiguration incident, a UK-based company exposed personal and payment data of several hundreds of its customers.
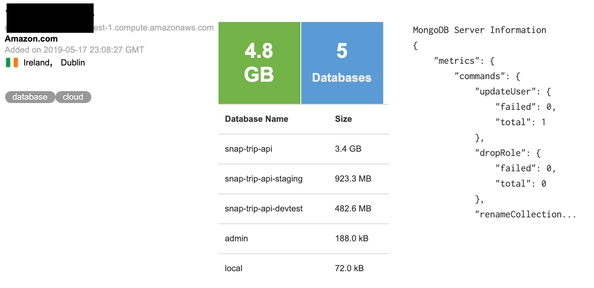
On May 21st, I have identified an open and unprotected MongoDB instance, with no password/login needed to view the data. IP with database has been indexed by Shodan, public search engine for IoT devices, on May 17th.
Upon verification, part of the database appeared to be production infrastructure of Snaptrip, “a marketplace aggregating over 60,000 professionally managed cottages from big-name partners“. As per their site, “Snaptrip is a trusted marketplace for people to discover the best last-minute cottage holiday deals in the UK“. Earlier in January 2019, Snaptrip has raised £2.1m and used a portion of the investment to acquire Last Minute Cottages – which includes the websites lastminute-cottages.co.uk, big-cottages.com and henpartyvenues.co.uk.
Among other information (like admin credentials and hashed account passwords), database named ‘Snap-Trip-Api‘ contained 1,006 records of what appeared to be personal and payment information of marketplace customers:
- Full name
- Phone number
- Full address
- CC details: brand/type/name/PAN token/CVV token
I have immediately sent an alert to the company handling the data and within hours database was secured. It is unknown whether the affected users or GDPR related authorities are notified – as of today, company representative did not return with answers to my questions
The danger of having an exposed (passwordless) MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.