On April 28th I discovered a dataset that contained what appeared to be customer information, payment references and was labeled as production data. There were links to sales records and links that identified the owner of the database was Lollicupstore. As soon as I could validate the data, I sent a responsible disclosure notice. Within an hour after sending the notice Lollicupstore acted fast and restricted public access to the database. I was unable to fully analyze the data because of how fast it was secured and because it contained over 112 million records. Our goal is always to help secure exposed data and it is often a race against the clock to responsibly notify the owners of the data we discover before it is compromised.
Unfortunately, no one replied to my initial notification which is sometimes normal as organizations conduct their internal investigations. However, on May 3rd I sent a follow up and then a final message on June 3rd that simply asked to acknowledge that my previous messages have been received. These messages also went unanswered.
We have long said that companies and organizations must do a better job to protect the data they collect and store. They have an obligation and a duty to notify users when they are involved in a data incident or have had their data exposed. Any data breach could potentially put customers at risk of a targeted phishing campaign or other social engineering scams. Today, customer data is just as valuable as the products or services a company sells. It is unclear if Lollicupstore notified customers, partners, or the authorities regarding the data exposure.
The database contained a massive 112 million records that were publicly exposed. There were many items that appeared to be client sensitive, including names, shipping information, email addresses and references to payment data. There was also internal records that exposed the business and was at risk for a ransomware attack. Internal logs, emails, and Magento eCommerce production logs including what appeared to be payment records.
What was in the database:
- This database was set to open and visible in any browser (publicly accessible) and anyone could edit, download, or even delete data without administrative credentials.
- 112,723,640 Million total records exposed
- Items that appear to be potentially client sensitive, including names, shipping related data, email addresses and other data.
- Internal records, logs, emails, password tokens, and other data
- IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper in to the network.
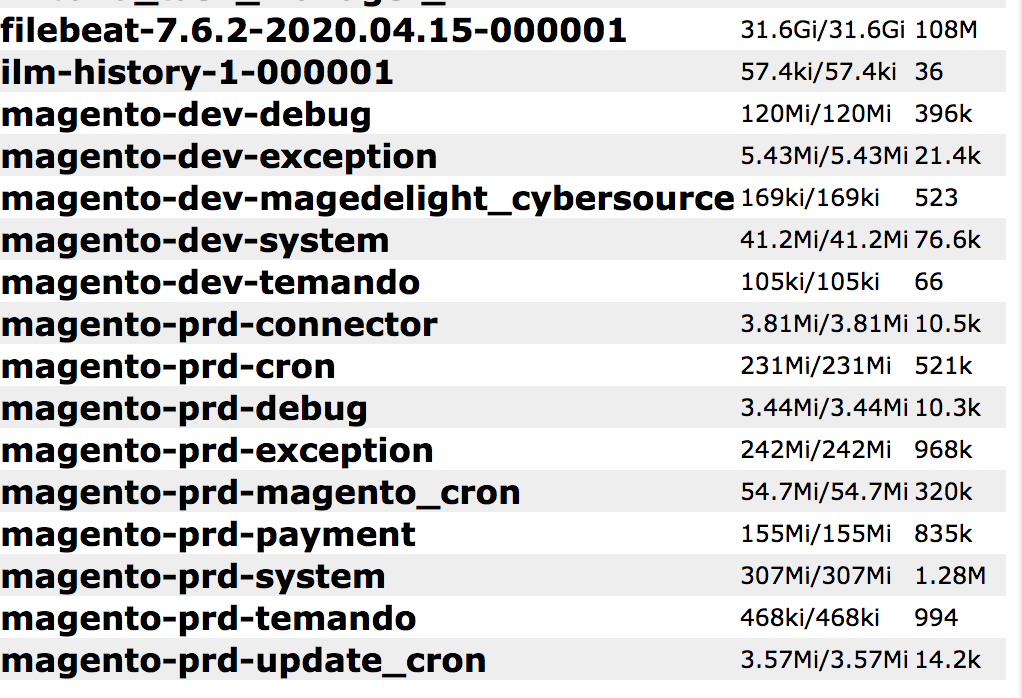
This data exposure highlights the dangers of online eCommerce software, the data it collects, and how that data is stored. The software does what it is programmed to, but the data it collects can be a point of exposure if misconfigured, leaked, or breached. The most disturbing number to me personally was just how many records were in the “payment” file with over 835k. It should be noted that I did not see credit card data in plain text and according to their website payments are processed via PayPal.
The danger of knowing someone is a customer and has made a purchase in the past opens the door for social engineering by criminals. Hypothetically a sale creates a point of trust with customers and a cyber criminal could contact that customer and say “we need to update your payment data, please give me your credit card information”. This sounds crazy that anyone would actually give their payment data, but people do it all the time. Theoretically the thief would have access to inside knowledge or sales data that only the company or organization would have. Social engineering and targeted phishing are dangerous because it involves a human element with information that only a person of trust should know.
Please note, I am not indicating or implying that customers are at risk or that this will happen. I am only presenting a scenario or possibility of how data could be abused by criminals.
According to Wikipedia: Lollicup Coffee & Tea is a Taiwanese American chain of tea shops founded by Lollicup USA, Inc., with headquarters in Chino, California. The company was founded in 2000 and currently has 38 branches in the United States and China.
As part of our responsible disclosure process we extend our assistance to organizations to help them understand how we discovered the data, any IP addresses used, time ranges, or answering any questions that may help their internal investigation process. This assistance is free of charge and much of the non-consulting research we do is not-for-profit or funded by bug bounties and discovery rewards.
Check out my most recent discovery: Texas Based Home Loan Provider Southwest Funding Exposes Database Containing 695k Records and Evidence of Ransomware.

