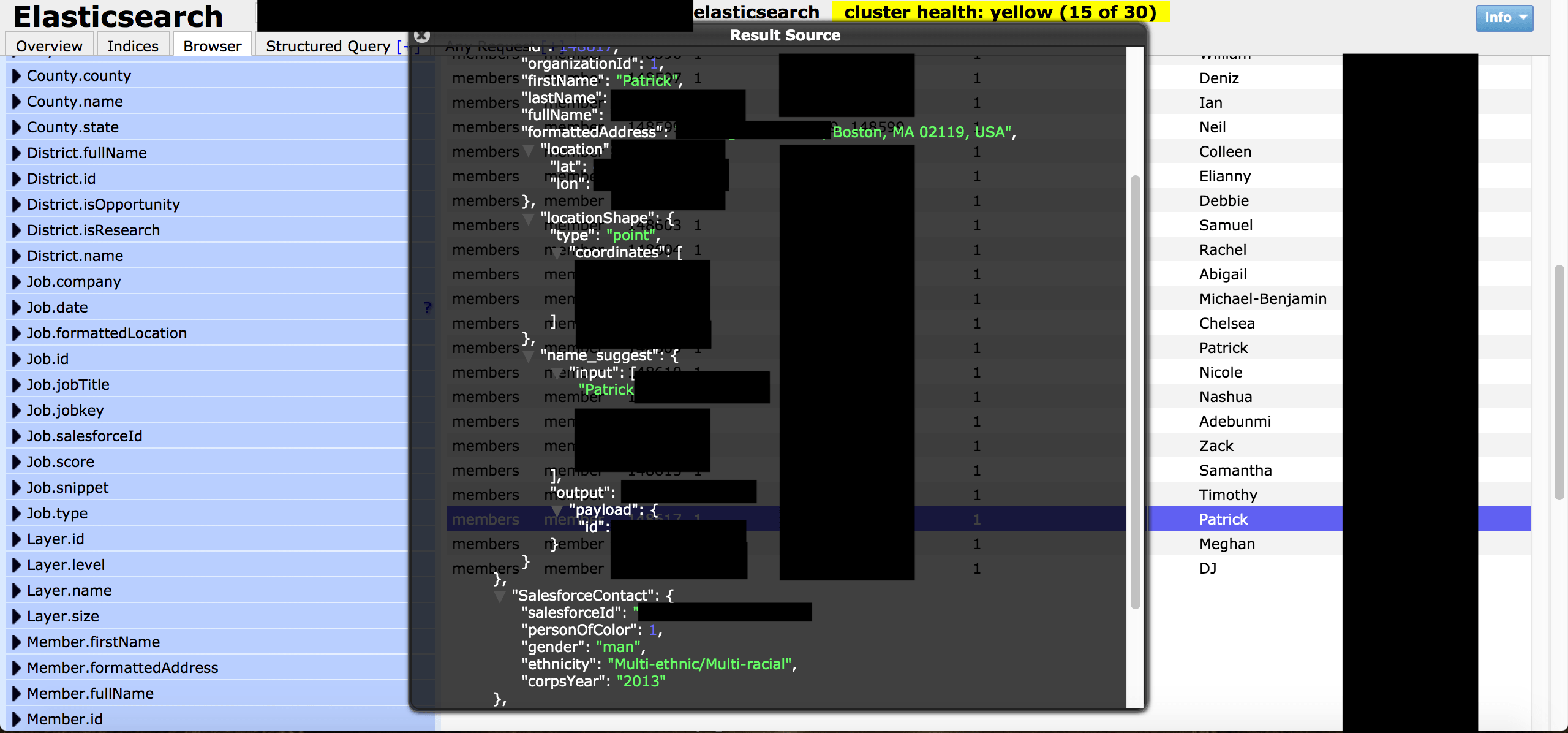
On July 26th discovered a non password protected elastic data set that contained 5.2 million documents in total. Immediately, I knew this information should not be publicly accessible and began trying to identify the ownership. Upon further investigation the data appeared to belong to an organization called Leadership for Educational Equity (LEE).
Leadership for Educational Equity (LEE) is a 501(c)(4) nonprofit organization based in Washington, D.C. LEE is a spin-off organization of Teach for America and was established in 2007. According to LEE, the organization seeks to address inequity in education by developing leadership skills among Teach for America members and alumni who, through leadership roles, could change education policy and can engage low-income communities to help bring about education reform.
According to their website: “Leadership for Educational Equity is a nonpartisan, nonprofit leadership development organization working to end the injustice of educational inequity by inspiring and supporting a diverse set of leaders with classroom experience to engage civically and politically”.
On July 27th I sent the first notification to multiple email addresses found inside the database and the contact listed on their website. Several days later I noticed that the data was still publicly accessible and no one had replied to my previous responsible disclosure notification. I then tried to reach them by phone leaving 2 separate voicemails. I stated in each message that it was regarding a data exposure and it was important that someone get in touch with me. The following day, I made a 3rd call and was able to get in contact with someone who passed the information to the correct person or team. Public access to the database was restricted shortly after my call.
I can confirm that the database remained open to anyone with an internet connection until at least July 31st. The names, addresses, and ethnic details of an estimated 3.6 million individuals was publicly exposed a minimum of 7 days. It is unclear exactly how long it was exposed or who else may have had access to the database before I discovered it. We can only speculate that the “members” folder was some sort of donor list or marketing outreach list. A representative for Leadership for Educational Equity reached out to us after our disclosure notice and responded fast and professionally in their communications and in securing the data.
Here is what we have discovered that included the following:
- This was an Elastic database set to open and visible in any browser (publicly accessible) and anyone could edit, download, or even delete data without administrative credentials.
- 3.69 million records of “Members” including names, home addresses.
- Salesforce ID, Gender, Ethnicity, Corps Year, Prospect information.
- IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper into the network.
Here is how the data appeared: 
We Focus on Data Security Not Politics:
As security researchers our mission is data protection, privacy, and we try to focus on only the facts of our discoveries. In the process of building any neutral and unbiased story we have to understand the organization and what they do with the data that we have discovered. However, when trying to learn more about “LEE” I was surprised to see multiple articles that focused on the political and lobbying efforts of Teach for America and Leadership for Educational Equity. Some highlighted the connection to Teach for America, open secrets information regarding donations, while others focused on the influential board members and donors (many of them are household names such as Walton, Bloomberg, Sackler, and others ).
I only mention this information because usually when a non-profit has a data incident it is often because of limited resources. We have seen multiple cases were charities and non-profits were so focused on their mission that they left gaps in their data protection or sadly they couldn’t afford security technology or personnel. In this case Leadership for Educational Equity does not seem to be struggling for resources. According to a 2017 tax filing posted by Propublica LEE’s total revenue was $29,626,462 and total expenses were $28,511,085. We do not cover politics or controversy but will include relevant information as pertains to the discovery and data privacy.
In Conclusion
Data incidents can happen to any organization large or small, well funded or struggling for funds. This discovery highlights once again that companies and organizations must do more to protect any information they collect or store. Another danger is that any data exposure could serve as a potential backdoor to access other areas deeper inside the network. As security researchers we never circumvent passwords and follow a responsible disclosure protocol with our discoveries. We should note that the database contained no highly sensitive data such as SS#, medical, or payment information.