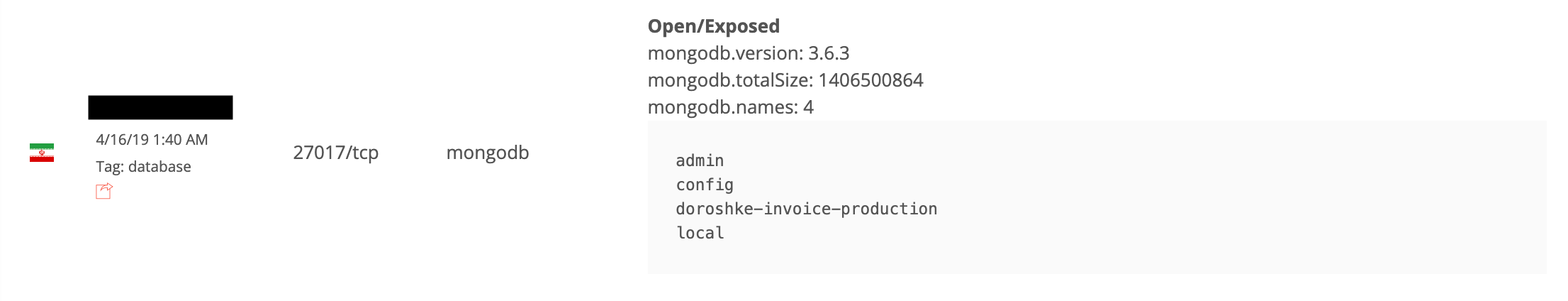
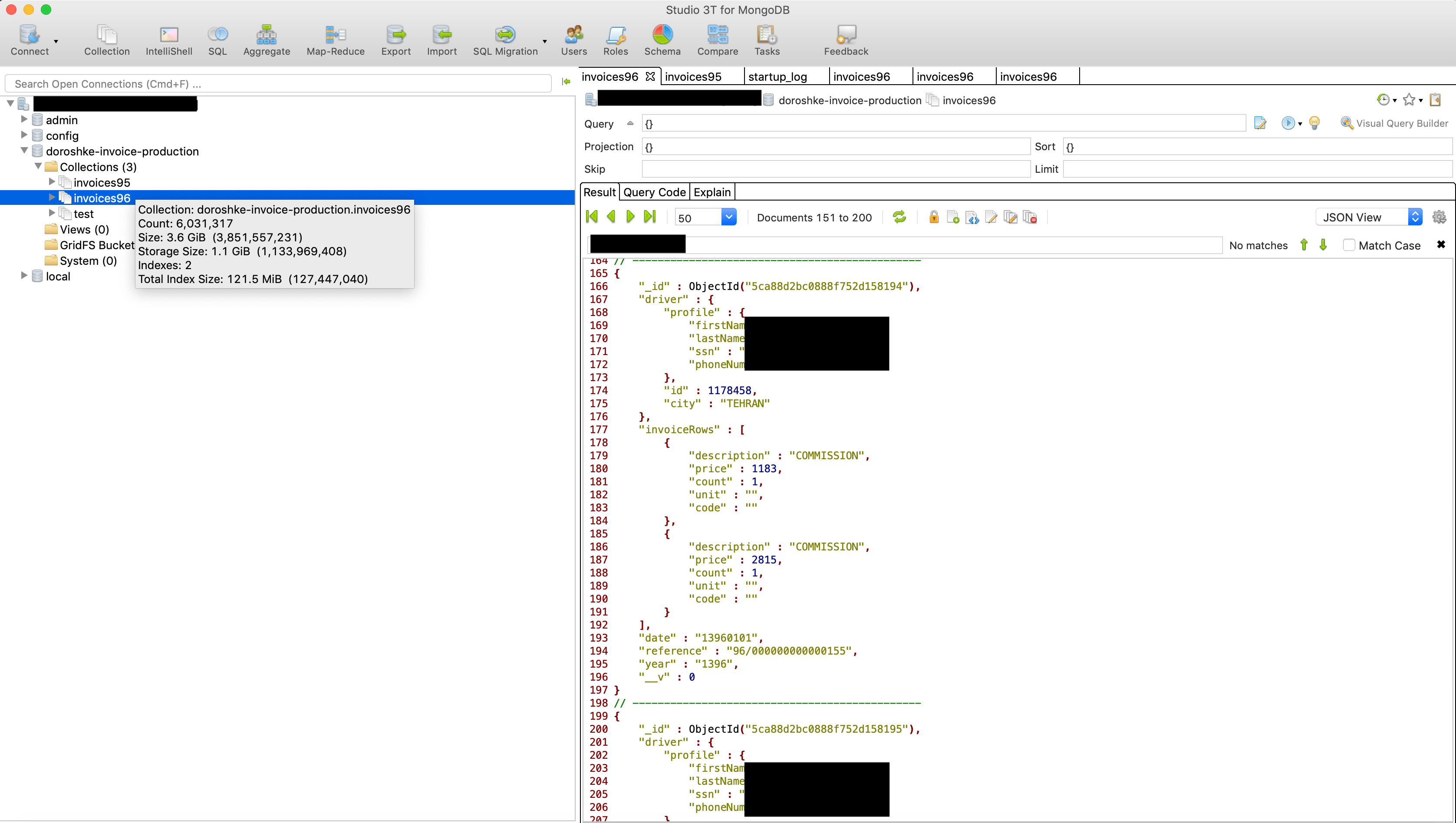
On April 18th, during our regular security audit of nonSql databases with BinaryEdge search engine, I have discovered an open and publicly available MongoDB instance which contained astonishingly sensitive information on Iranian drivers.
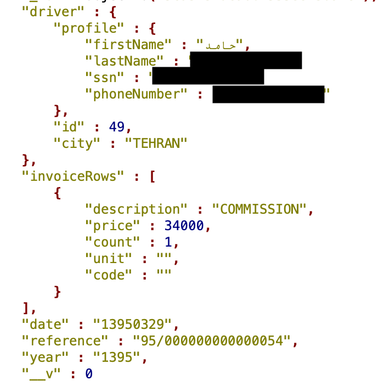
Information was structured to include the following data fields:
- Driver first name and last name
- SSN (10-digits Iranian ID number in plain text)
- Phone Number
- Invoice date
Database named ‘doroshke-invoice-production‘ (doroshke means carriage in Persian) had two collections with invoices split by year:
- invoice95 (all the invoices from year 1395, which corresponds to 2017 in Gregorian calendar), with total number of records: 740,952
- invoice96 (all the invoices from year 1396, which corresponds to 2018 in Gregorian calendar), with total number of records: 6,031,317
Estimated total number of records exposed: 6,772,269
Please note that the total number of records might not be representative of the total number of affected people, since there could be duplicates (I am still analyzing the samples), but from what I’ve seen, each record was unique.
[UPDATE] I have recorded duplicates in the dataset, so the estimated number of unique entries is about 1-2 Million.
No company affiliation was available throughout the records.
I have immediately sent an alert to the Iranian CERT and also initiated own investigation with the assistance of dedicated security researchers on the ground. We were able to get in touch with a couple of drivers with an attempt to identify the owner of the database. At the same time, my colleagues have reached out to the biggest ride-hailing companies in Iran to confirm data origin.
While I did not receive an official confirmation or comment from either company, we can only guess if this data was part of their infrastructure. However, no matter who owned it, the fact alone that such highly sensitive PII (personally identifiable information) was available in the wild for at least 3 days, is scary.
Chances are also big that this data was stolen previously from either company and now resurfaced – as a result of human error in malicious database.
This report will be updated if/when more information is available.
Danger of having exposed MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
Here is a background of work / researches that I do. To discover data breaches, leakages, and vulnerabilities on the Internet, I use public search engines only, such as Shodan, Censys, BinaryEdge etc. When I find a public database or any other instance (data that’s fully accessible to anyone without any restrictions) I collect several digital samples for further analysis. If these samples contain any kind of private and sensitive data, I employ a Responsible Disclosure model to privately communicate the findings with data owners (the company or organization that left the information publicly accessible) and help them implement specific security safeguards to protect their private data.