FamilaFacil, a Madrid-based home and family job search platform, has exposed its MongoDB database with details on their users and candidates. This was the first time I discovered an unprotected instance sitting in IPv6 environment – as indexed by BinaryEdge platform (who recently added IPv6 search into their offering).
Database was first spotted in public on August 13th and consequently closed down the next day.
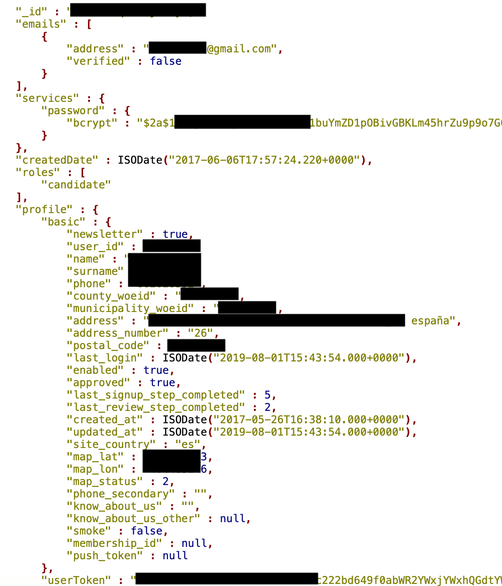
The following information related to FamiliaFacil customers was left visible for anybody who knew where to look:
- 551,587 records with customer contact details, such as name, email, phone, address, picture and bcrypted password
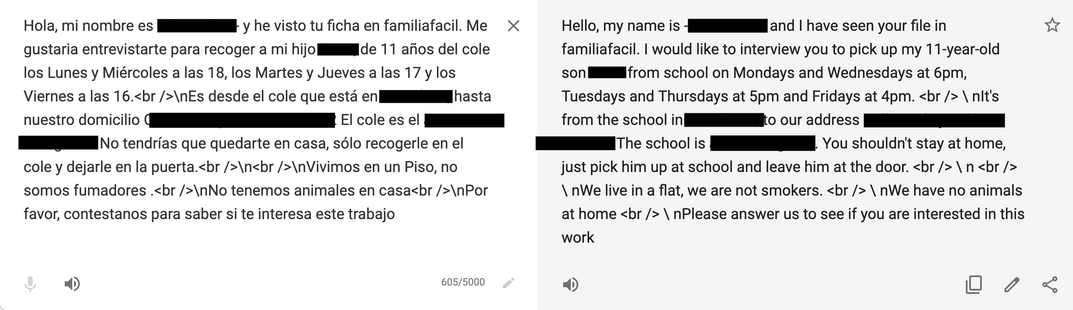
- 1,720,408 private messages sent to job seekers by requesters
- 1,548,767 public chat records
- and many more
As I mentioned, database was quickly pulled offline and FamiliaFacila CTO who was very responsive provided me with the following statement:
We are lucky as this is only a ‘cached modified copy’ of our main database; a trimmed-down version with another data structure pre-processed to make mobile apps faster. The only thing I don’t understand is “password” field, as it’s not available in the app. Maybe the provider reused a standard (old) development and that field was left there or reused with other purpose.
It is unknown, whether somebody else has accessed the data while it was set to public, but if you are FamiliaFacila customer it is worth changing your password (and make sure you do not reuse the same password for other accounts, such as your email etc).
Danger of having exposed MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
***
As we see a never-ending loop of these incidents, we at SecurityDiscovery.com have decided to offer a live educational session (webinar or offline workshop) for raising cyber security awareness within your organization, to prevent potential issues in the future. We use real world examples and promote that data security is important to every employee and at every level inside the organization.
It can be an online webinar session (estimated 1h long), with Q&A session or an offline meeting in your offices, live interaction with your team (master class included).
Proposed content includes
- Description of tools and techniques we use to identify vulnerabilities, PII and sensitive data online: no hacking, just google-it.
- How to ensure your data / your company’s data is not exposed to the public internet, security tips from professionals
- Recommendations and best practice on main noSQL databases configurations and maintenance (MongoDB, CouchDB, Elasticsearch)
- Case studies: analyzing related data appearance online
- Live search for data and master class (for Option 2 only)