Recently I discovered an open and non-password protected database that contained 12,976,279 records. The total size of the dataset was 58 GB and contained content management data, including employees PIIs. Upon further research nearly all records contained information indicating FOX content, storage information, internal FOX emails, usernames, employee ID numbers, affiliate station information and more. The records also captured a wide range of data points including event logging, host names, host account numbers, IP addresses, interface, device data, and much more.
The environment was listed as “CMS” and we did not see any references to test or demo inside the records. The digital asset management database shows a detailed look at the internal collaborative environment divided by users, administrators, and content.
What the database contained:
- Total Size: 58.03 GB
- Total Docs: 12,976,279
- Many references to “theplatform” and links that redirect to Comcast Technology Solutions and all of the content was FOX related. (ThePlatform is an online video management platform that manages, monetizes, and syndicates video views for media companies).
- Internal CMS records of FOX that exposes user IDs, event logging, host names, IPs, interface and device data. Many of the records are labeled Production.
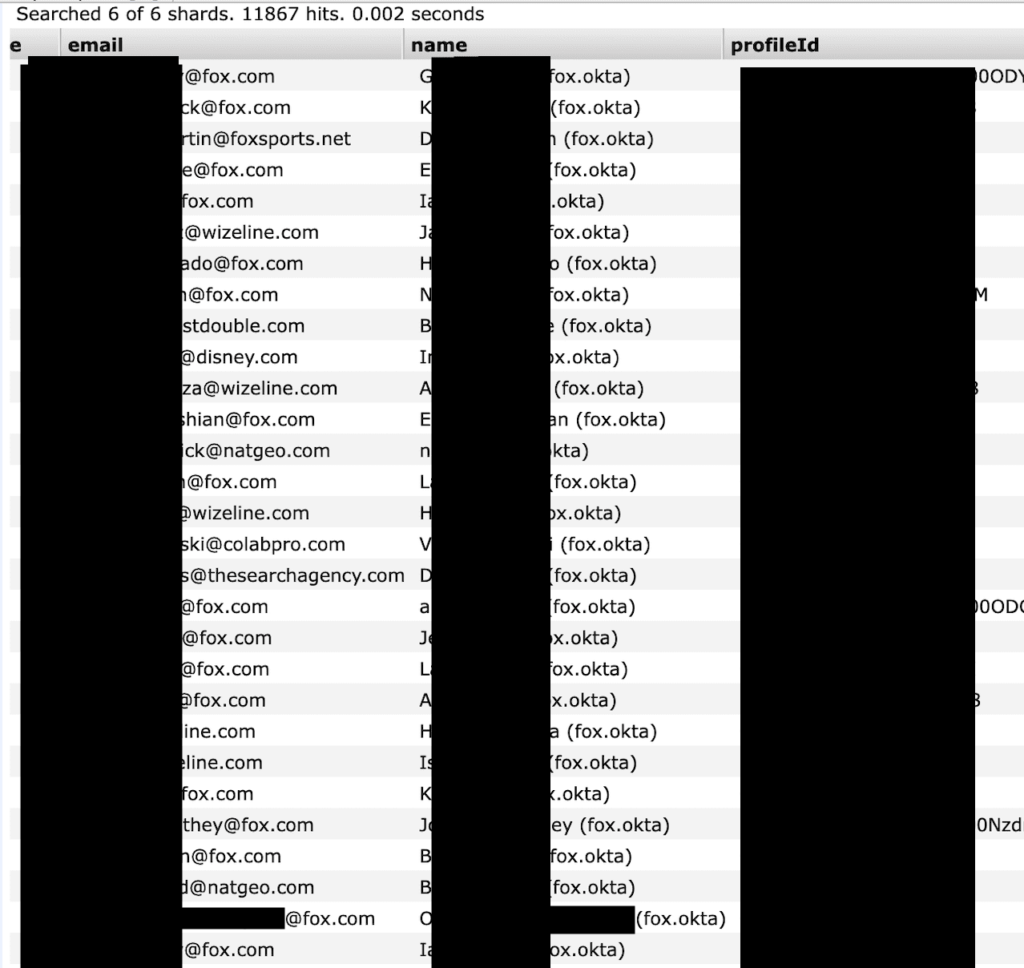
- Large number of email addresses of users including 701 internal @fox.com email addresses that could be at risk of a targeted phishing campaign. These emails also include internal ID numbers and security or user roles.
- The files also show where data is stored, content delivery paths, and served as a virtual blueprint of how the network operates from the backend. There were also links to FTP (File Transfer Protocol) and content storage locations.
- The non-password protected and unencrypted database was at risk of a ransomware attack that would encrypt the data. The exposed environment is marked as “CMS” and could allow cyber criminals to insert malicious code or identify vulnerabilities for a future cyber attack.
The FOX Security Team acted fast and professionally to close access to the unsecured and publicly exposed database. It is unclear how long these records were exposed or who else may have had access to the dataset. As security researchers we never extract or download the data we find and only take a limited number of screenshots for validation purposes. We are not implying any wrongdoing by FOX, Comcast Technology Solutions or their partners. Nor, are we implying that any customer or user data was at risk.
You can view my full report here.
