Booking a hotel online is now so common that we consumers never give it a second thought when traveling. We enter our information, provide payment details and then cross our fingers. Unfortunately once we provide our data to a company or organization we no longer have control over how our personal details are stored.
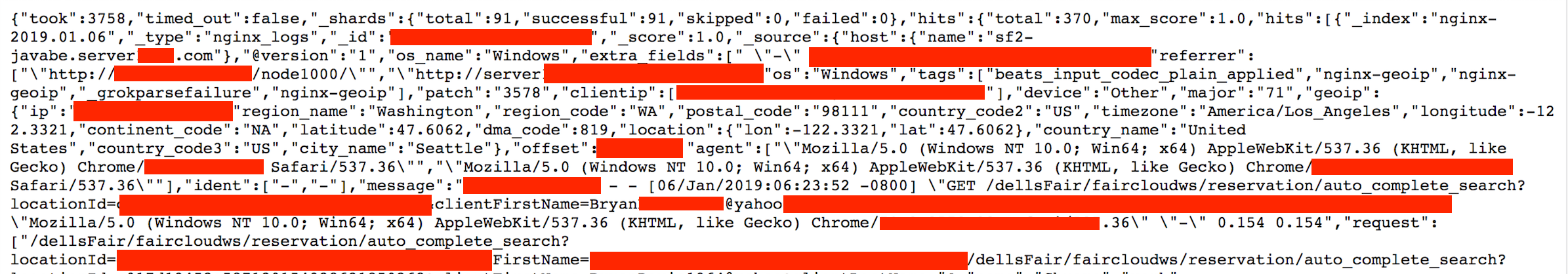
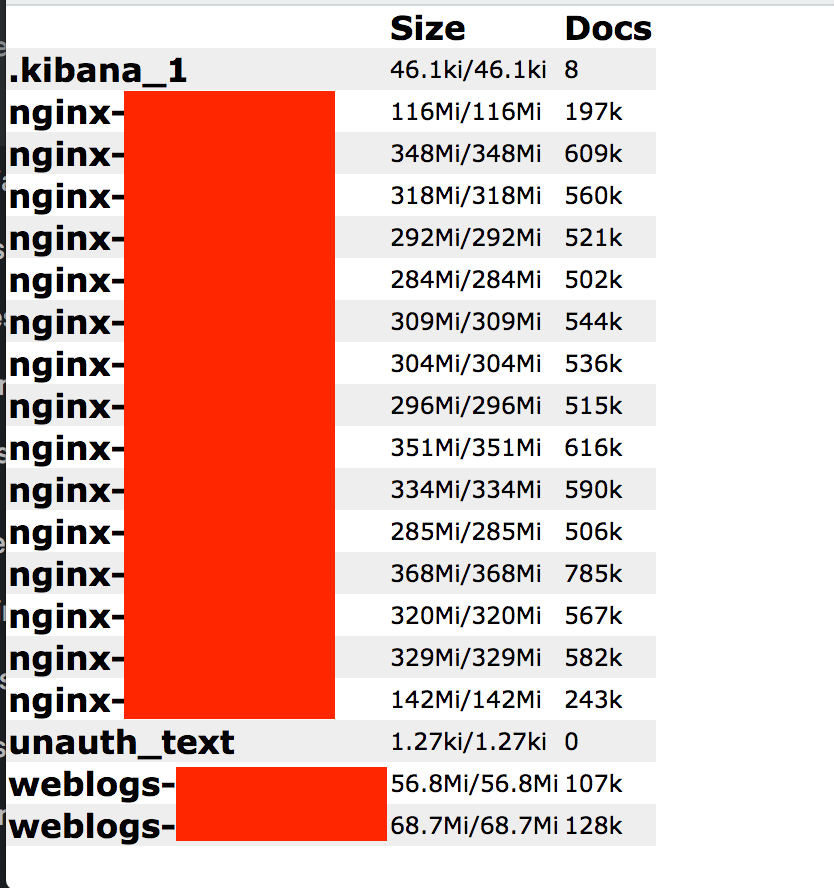
On December 11th I discovered a non password protected database that was open and publicly accessible database that belonged to FairBridge Inn & Suites that contained an estimated 8.1 million records. A vast majority of the records were Nginx logs and some contained hotel guest data. Nginx writes records of its events in two types of logs: access logs and error logs. Access logs write information about client requests, and error logs write information about the server and application issues.
In a phone call with a representative from FairBridge Inn & Suites he confirmed ownership of the database and informed me that it contained an estimated 150,000 individuals.
Here is what we discovered:
- Estimated 8.1 Million NGINX Log records
- Customer Emails, Reservation Numbers, Customer IP and location data, Employee ID and additional records that should not be exposed online.
- Estimated 150,000 customers affected.
- IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper in to the network.
According to their FaceBook page: “FairBridge offers complete branding solutions for hotels seeking attractive & affordable licensing programs featuring leading-edge revenue support services for operators across all market segments.Powered for success by our dynamic technology platform and unique delivery model, FairBridge re-aligns, revitalizes, and re-brands hotels to perform better for less”.
FairBridge Inn was founded in 2009 and FairBridge Inn’s headquarters is located in Spokane, Washington. According to their website they have 37 locations in 24 states. It is unclear how long the data was exposed or who else may have had access to the publicly exposed database. It is also unclear if customers or partners have been notified of the exposure.