A database belonging to online voting system provider Everyone Counts has been exposed, leaving what appears to be “randomized and anonymized” data used to simulate millions of voters and election workers open to the public.
The database, which belong to Everyone Counts, was erroneously exposed to the public for around three days such that anyone with an internet connection could view its contents. I uncovered the exposure on July 5, 2019. The data leak involved a MongoDB database that was publicly available.
Everyone Counts, which was acquired by Votem in 2018, provides election software designed to improve the security, efficiency, and reliability of voting processes. The records in the exposed database contained randomized and anonymized personal information about voters (all of whom are from the state of New Jersey, based on my observations) and election workers.
Timeline of the data leak
For some reason, the MongoDB database was made publicly available with no authentication required to access it.
As a result, it was indexed by search engine BinaryEdge. This means it was available to anyone online. The database was first indexed by the search engine on July 4, 2019.
I discovered the exposed information on July 5, 2019. The company email addresses associated with “superAdmin” records were from the domain “everyonecounts.com” which led us to believe this database was administered by Everyone Counts.
I tried to contact the assumed owners of the database, via an email sent to five members of the Everyone Counts team on the evening of July 5, 2019. Later I was contacted by a representative of know ink, who has recently taken over the contract from votem, and was provided with the following statement:
Thank you so much for alerting us to this. The database in question is a fictitious test database environment we use with scrambled record data and randomly generated values for items such as first and last names, birthdates and SSN’s. This data was not meant to be publicly accessible, but it highlights the importance of anonymizing information to scramble and remove PII.
In responding to the reported incident, the software company responsible for developing and maintaining the Voter Registration system investigated the source of the data and determined that “there was not in fact a security breach of the data used for the Voter Registration system and contained no production data, including non-working user ids. As it contained fake data that was generated to simulate data in the Voter Registration system”.
The database was secured on July 6, 2019 and is no longer exposed.
Also unknown is whether or not any malicious parties accessed or copied the fictitious test data while it was available.
What information was exposed?
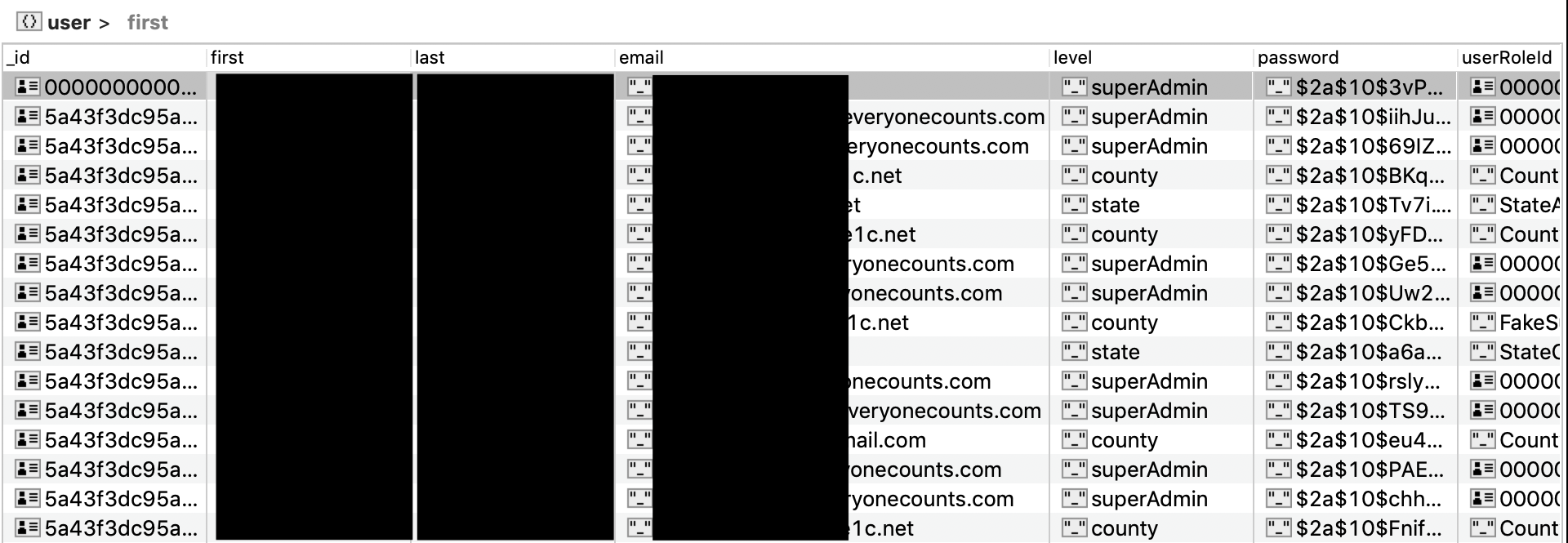
The database held fictitious test data that was generated to simulate more than 85,000 scrambled and randomized voter and election worker records and over a dozen sets of administrator credentials which appear to have bcrypt hashes salted. All of the generated voter records observed related to fields consistent with those in the state of New Jersey’s voter records. Here’s what was included in each voter record:
- Voter status
- Party
- Full name (fictitious generated names)
- DOB (and DOD if deceased)
- Residential address
- Voting preferences
- Phone number
- Email (not every record included this)
- IDs (driver’s license number in some cases)
A Social Security Number (SSN) field was present but had null values.
According to the Everyone Counts website, the company was awarded a 10-year contract by the state of New Jersey Division of Elections to manage its voter registration system. It appears that the exposed database contained data about all of the voters registered statewide but the data had been scrambled so that you could not match addresses to peoples names and important information such as birth dates or SSN’s had been randomly generated.
85,886 election worker records contained the above information in addition to SSNs which had been randomly generated for development.
16 sets of administrator credentials were also visible. These included old, non-working usernames and email addresses and encrypted passwords.
Potential implications of leaked test information
Even test data can have valuable information contained within it. Items such as email addresses can be used for phishing techniques. Knowing a list of all usernames can give you a first step to cracking into a workers full account.
One positive here is that the exposed administrator passwords were encrypted and the user ids were all non-working test accounts. That being said, passwords associated with known usernames can often be determined using brute force attacks or credential stuffing using information from past data breaches.
Luckily enough for NJ State Vendor, this data seems to have been scrambled and anonymized correctly. Even with test data; one thing that cannot be randomized is the underline table schema and data structure. Having this information makes it much easier for people to reverse engineer and run malicious code on the actual system similar to sql injection.
About Everyone Counts
Everyone Counts Inc. was founded in 1996 and offers a Software-as-a-Service (SaaS) platform providing electronic voting solutions. In late 2018, Everyone Counts was acquired by Votem, a company that offers online and mobile voting platforms, including voting software centered around blockchain technology.
To date, neither Everyone Counts nor Votem appears to have been affected by a data leak. However, Votem, and by extension, Everyone Counts, hasn’t escaped negative press entirely. In February 2019, shortly after the Everyone Counts acquisition, Votem made the news for abruptly closing its California office, reportedly due to lack of funding.
Since then, the future of the company remains uncertain, although it maintains it is still servicing clients. To add to its woes, a class-action lawsuit was filed against CEO Pete Martin in April 2019, as laid-off workers seek compensation for unpaid wages and additional costs.
At one point, the City of Los Angeles was considering extending its relationship with Everyone Counts (along with new parent company Votem). This prompted speculation from an LA-based community activist that the acquisition and subsequent events may lead to sensitive voter data being put at risk.
Voter data security
This isn’t the first data exposure involving voter information. In the leadup to the 2018 midterm elections, voter information for around 35 million US citizens was up for sale on a hacking forum. And in 2017, 198 million voter records were left unsecured online for almost two weeks.
These are just a couple of examples highlighting the struggle to secure this valuable information. Companies like Everyone Counts and Votem claim to offer secure platforms and are no doubt trying to deliver just that. However, as their own technology advances, so does that of cybercriminals. For one, “uncrackable” encryption doesn’t remain that way forever. Factor in human error—which likely played a role in this instance—and it’s difficult to make any guarantees.