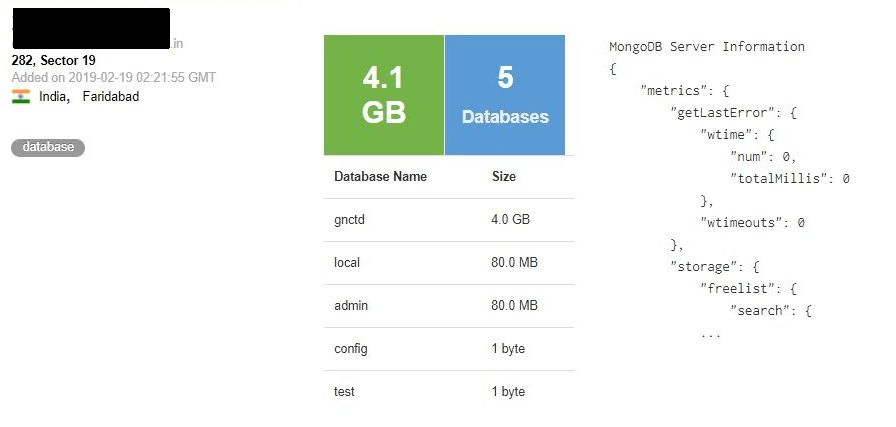
On Feb 19, 2019, I have discovered a MongoDB that required no password. The database was located in an India region which (along with other data) also contained highly sensitive information collected on 458,388 individuals located in Delhi. A 4.1GB-sized database had been indexed by Shodan and was left unattended for public access.
The database was named “GNCTD” which also stands for Government of National Capital Territory of Delhi and contained the following collections and records:
- EB* Registers
- EB Users (14,861)
- Households (102,863)
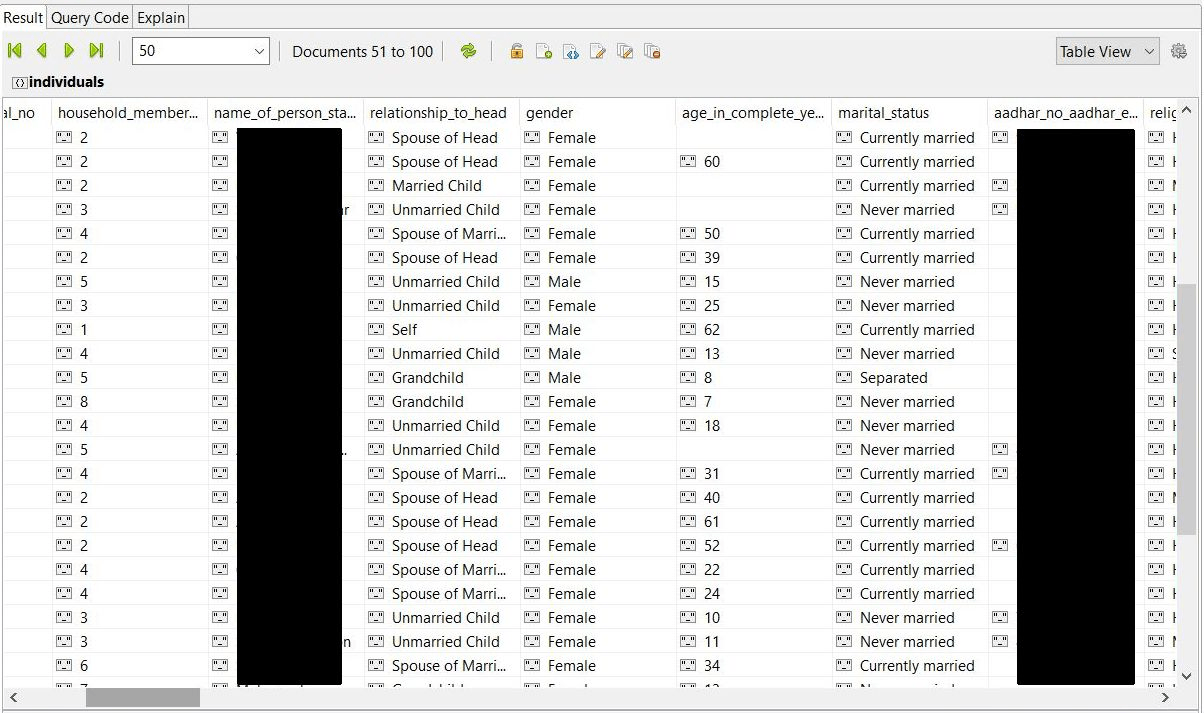
- Individuals (458,388)
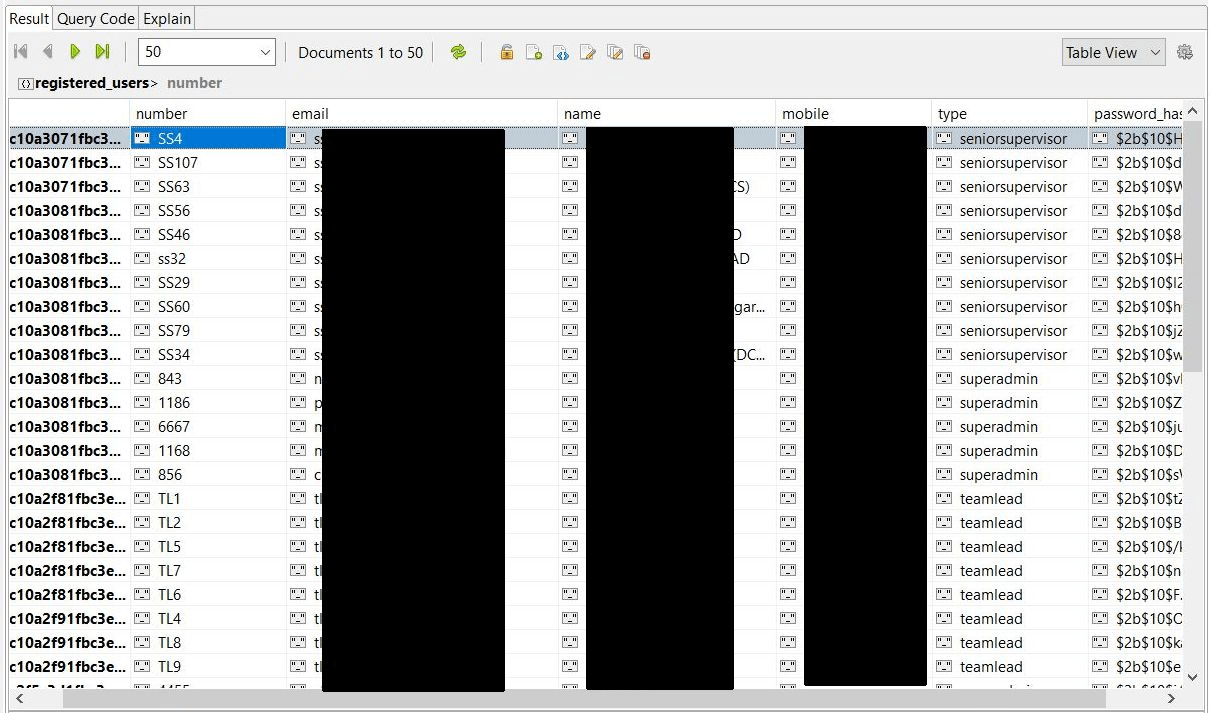
- Registered Users (399)
- Users (2,983)
*EB should stand for ‘enumeration block’ which is the lowest administrative unit in India.
After analyzing the content I have come to the conclusion that database appears to be somehow related to a company named Transerve. All the collections, including ‘registered users’ and ‘users‘ contained references and emails with ‘transerve.com‘ domain, as well as hashed passwords and usernames for administrator access.
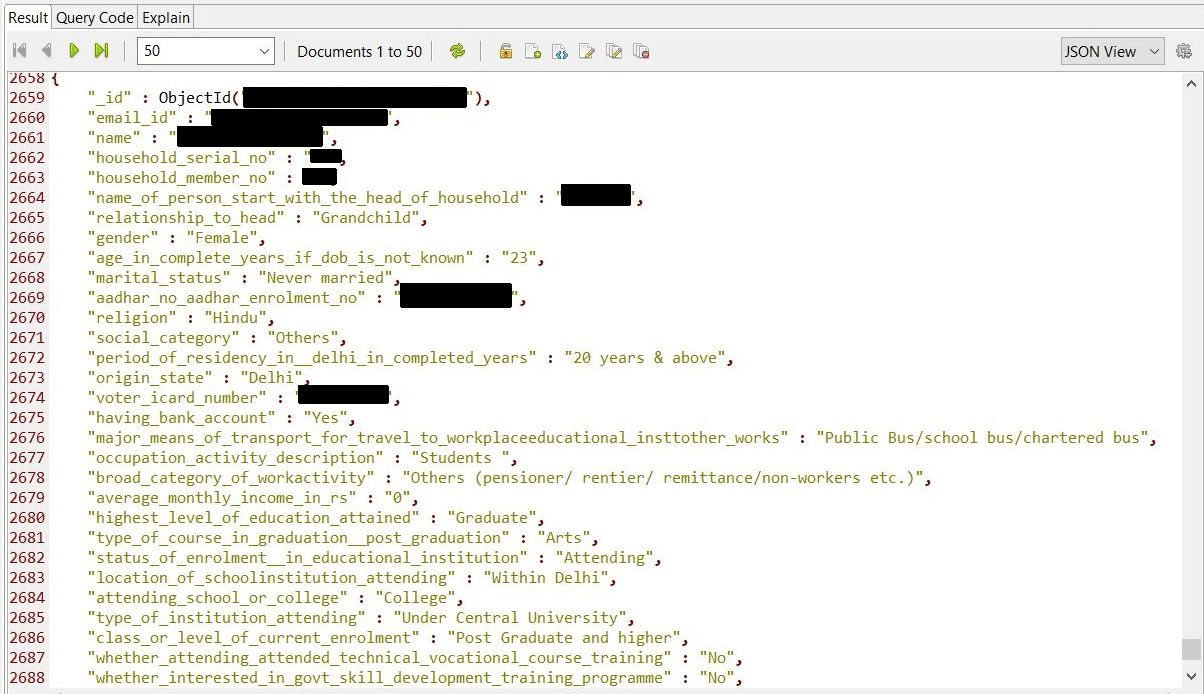
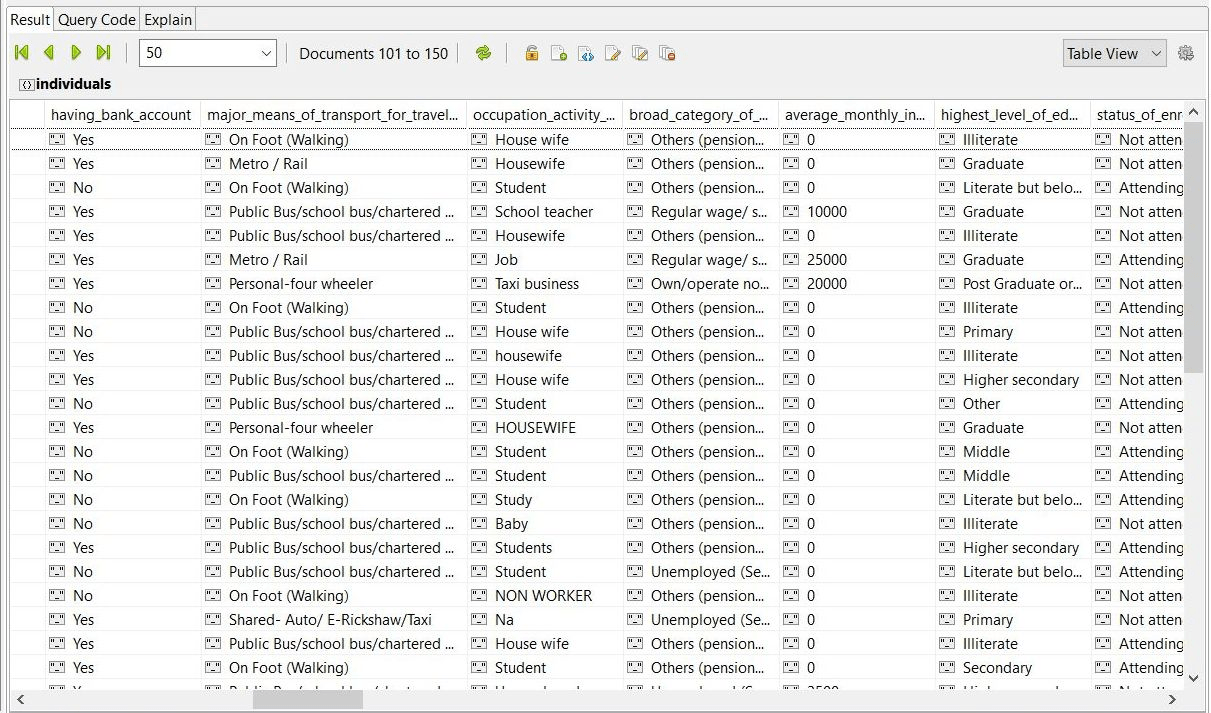
The most detailed information contained in ‘Individuals’ collection which was basically a pretty detailed portrait of a person, incl. Aadhaar numbers, voter card numbers, health conditions, education, etc.
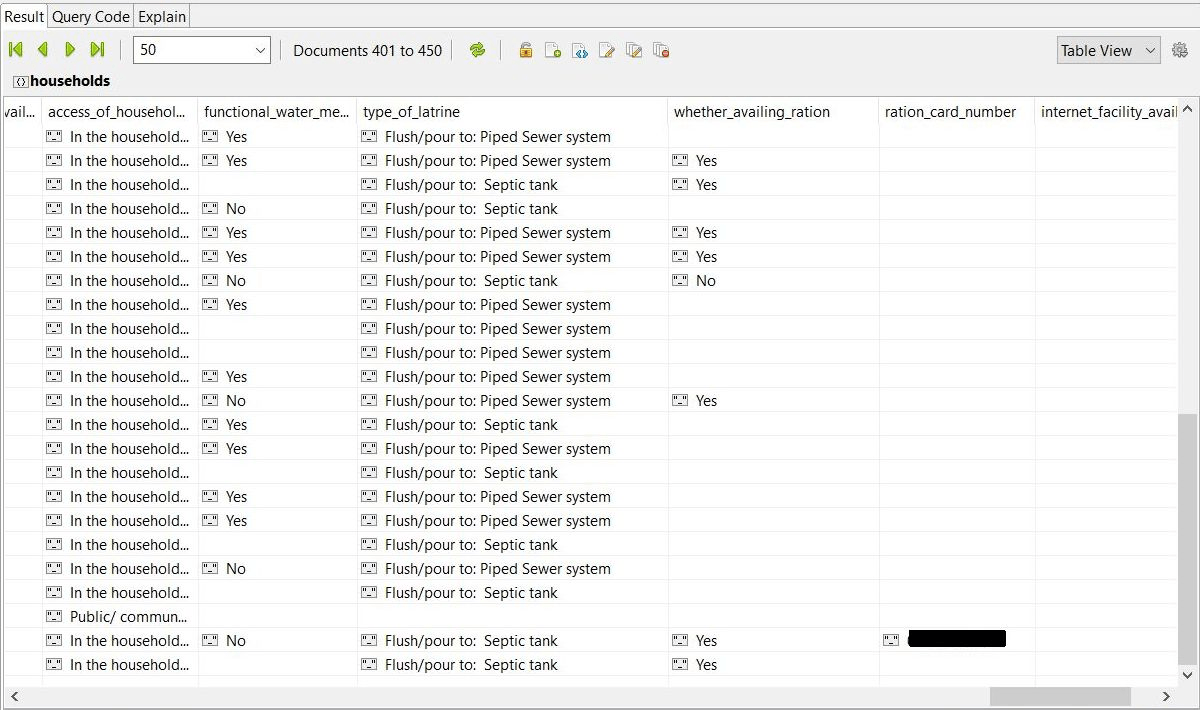
“Households” collection contained fields such as ‘name’, ‘house no’, ‘floor number’, ‘geolocation’, area details, ’email_ID’ of a supervisor, ‘is the household cooperating for survey’ field, ‘type of latrine’, ‘functional water meter’, ‘ration card number’, ‘internet facility available’ and even ‘informan name’ field.
According to their site, Transerve “offer solutions to make cities smarter, sustainable and effective in operation to impact the quality of life”. It is also ‘”democratizing data through Transerve Data Collector”.
We cannot say for sure that this database is connected to GNCTD, but that is highly likely based on the evidence.
I immediately sent a notification email to several Transerve contacts (found in database and online), however, received no response. Only after I contacted CERT India, database has been secured and taken offline. CERT is the Indian Computer Emergency Response Team is an office within the Ministry of Electronics and Information Technology. It is the nodal agency to deal with cyber security threats like hacking, phishing, and data protection.
It remains unknown just how long database was online and if anyone else accessed it. I will update this post if any additional information comes in.
The danger of having an exposed MongoDB or similar NonSql databases is a huge risk. We have previously reported that the lack of authentication allowed the installation of malware or ransomware on thousands of MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
These attacks are able to occur because the MongoDB database is remotely accessible and not properly secured. This means that these attacks are easily prevented by following fairly simple steps in securing the database instance.
About author and security researcher:
Bob Diachenko has over 12 years experience working in corporate/product/internal communications with a strong focus on infosecurity, IT and technology. In the past Bob has worked with top tier media, government agencies, and law enforcement to help secure exposed data. Follow Bob on Twitter and his blog on Linkedin, Email: [email protected]