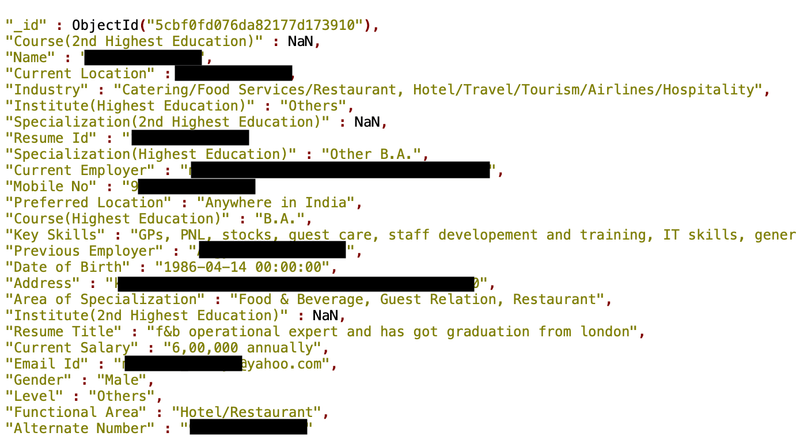
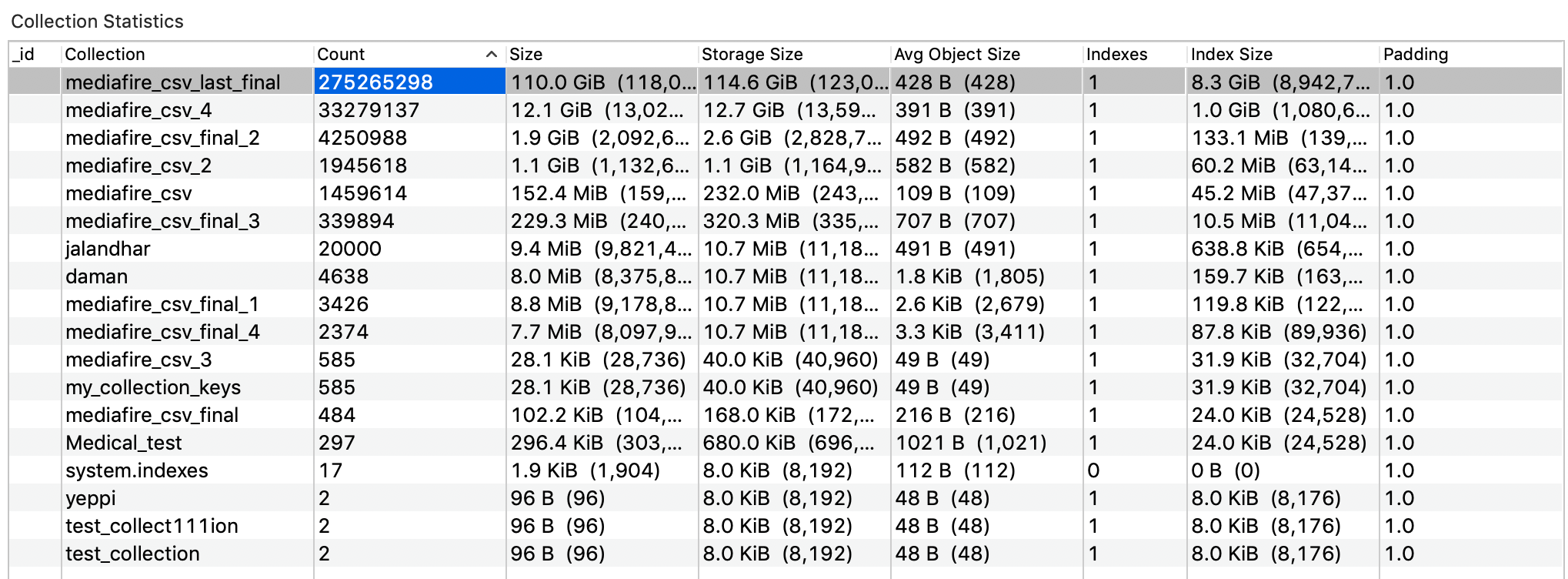
On May 1st, I have discovered an unprotected and publicly indexed MongoDB database which contained 275,265,298 records with personal identifiable information (PII) on Indian citizens, including the following fields:
- Name
- Gender
- Education level and area of speciazliation
- Professional skills / functional area
- Mobile phone number
- Employment history and current employer
- Date of birth
- Current salary
There was no indication in the database about the owner of data or affiliation tags. MongoDB itself was hosted on Amazon AWS infrastructure, and reverse DNS also showed no results.
The structure and names of the collections in the database hinted that data was likely collected by anonymous person or organization as part of a massive scraping operation:
According to Shodan historical data, MongoDB was first indexed on April 23, 2019.
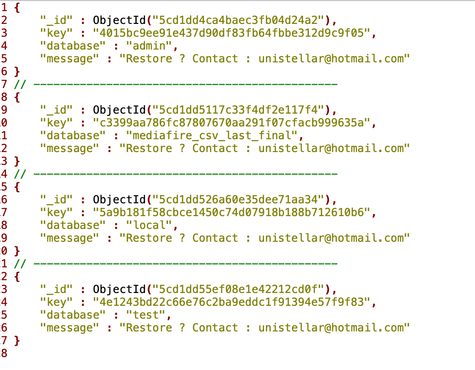
I have immediately notified Indian CERT team on the incident, however, database remained open and searchable until today, May 8th, when it got dropped by hackers known as ‘Unistellar’ group. All the content was wiped out and the following message appeared:
While the actual number of exposed persons might be less than the total number of records exposed, it is still one of the biggest breaches reported in the region. Absence of the affiliation don’t make this incident low-profile.
I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
See my insights on this issue here.