In another Elasticsearch misconfiguration incident Credia.ge, a Tbilisi-based (Georgia) agency, exposed personal and loan information for thousands of its customers.
I have identified the publicly available Elasticsearch cluster on August 3rd, however, according to Shodan historical data, it was first indexed back in September 2018. Moreover, there was at least one more database set to public on adjacent IP.
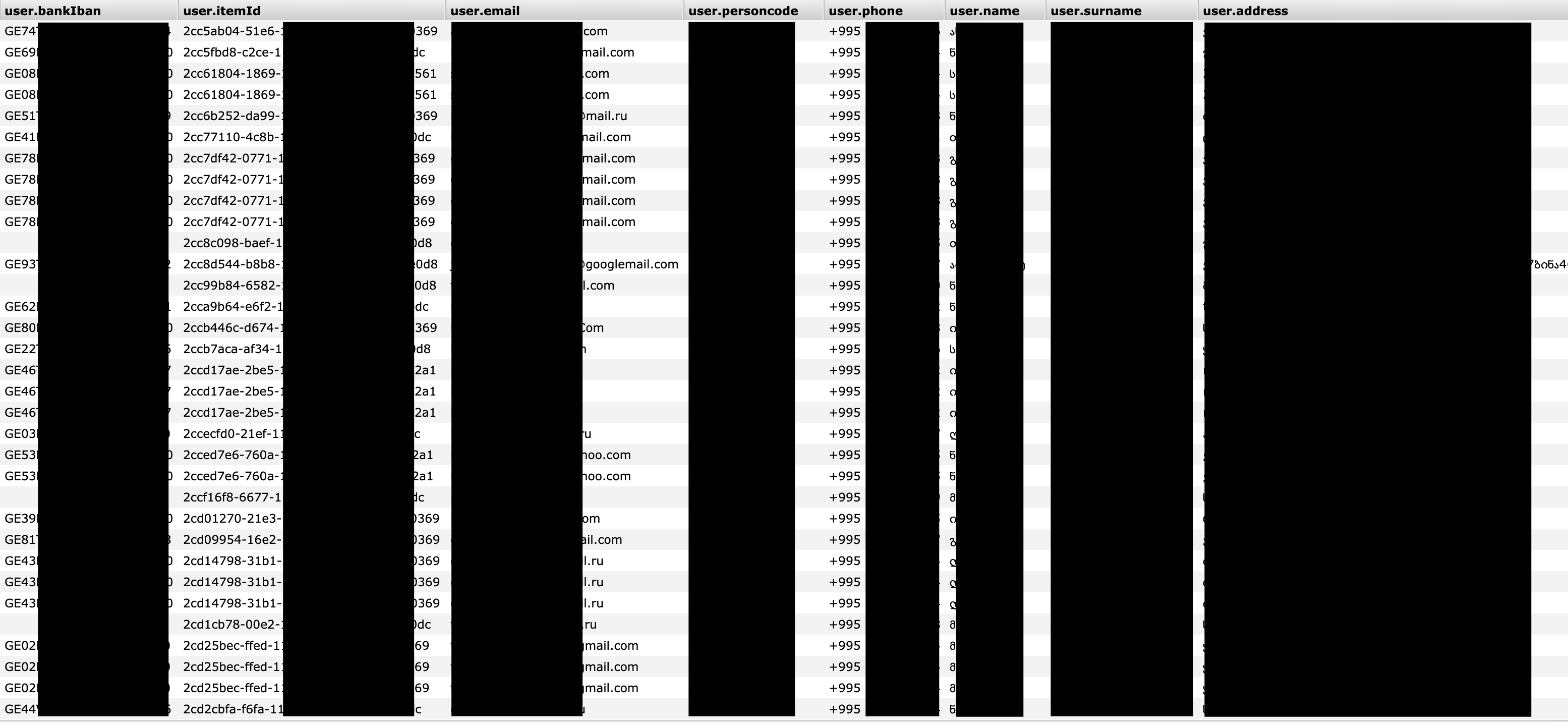
A 2GB Elasticsearch in question already was labeled as ‘compromised‘ in Shodan search and contained 142,571 user records the following information:
- Username (full name)
- Full address
- Birth day/month
- Passport number
- Loan amount (if granted)
- Tax ID code
- IBAN bank number
- Unicard ID (if applicable)
- Loan status (denied/granted)
Loan collection contained 12,416 records, with similar data – however, each line appears to be unique in that one. Application collection had 229,474 records, with additional details on loans and deny reason and deny methods.
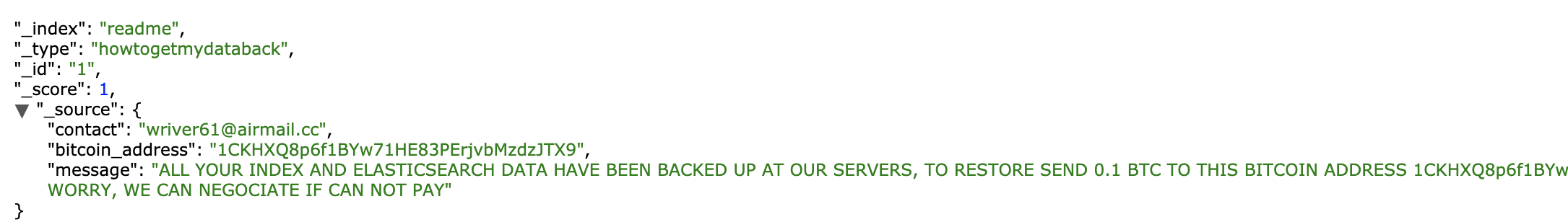
On top of that, a Readme note was found, with ransom demand for 0.1 BTC for returning the data (which was not deleted for some reason).
I have immediately sent a responsible disclosure alert to the organization, but no response was ever received. On August 9th (almost a week after the initial discovery) database was still open, so I got in touch with Georgian CERT authority and the same day database was pulled offline.
Worth noting that in June 2019, Credia.ge company has started liquidation process.
It is unknown, whether somebody else has accessed the data while it was set to public (since last year, obviously), but the chances are high that this information had been exfiltrated at some point.
Danger of having exposed Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the Elasticsearch servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
***
As we see a never-ending loop of these incidents, we at SecurityDiscovery.com have decided to offer a live educational session (webinar or offline workshop) for raising cyber security awareness within your organization, to prevent potential issues in the future. We use real world examples and promote that data security is important to every employee and at every level inside the organization.
It can be an online webinar session (estimated 1h long), with Q&A session or an offline meeting in your offices, live interaction with your team (master class included).
Proposed content includes
- Description of tools and techniques we use to identify vulnerabilities, PII and sensitive data online: no hacking, just google-it.
- How to ensure your data / your company’s data is not exposed to the public internet, security tips from professionals
- Recommendations and best practice on main noSQL databases configurations and maintenance (MongoDB, CouchDB, Elasticsearch)
- Case studies: analyzing related data appearance online
- Live search for data and master class (for Option 2 only)
Please feel free to send your requests to alert(at)securitydiscovery.com or bob(at)securitydiscovery.com
Let’s educate your team!