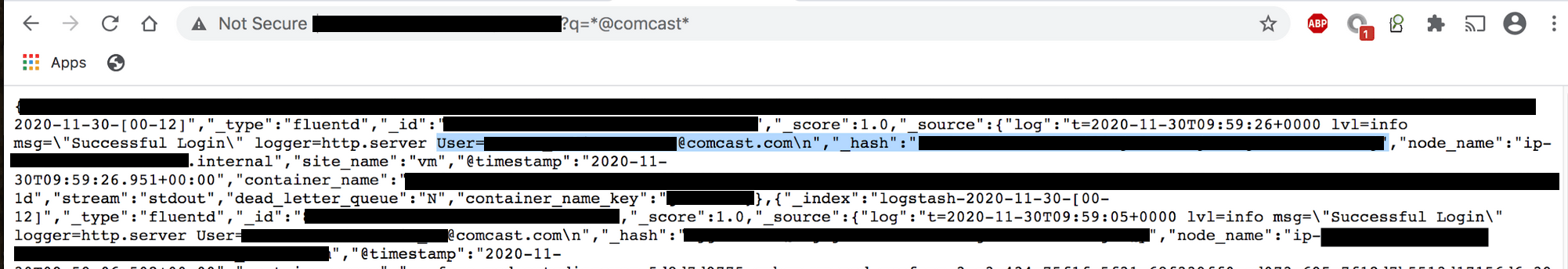
On December 1st, 2020 I discovered a non-password protected database that contained over 1.5 billion records. Inside the dataset were clear references to Comcast that included subdomains, urls, and internal IP addresses. The publicly visible records included dashboard permissions, logging, client IPs, @comcast email addresses, and hashed passwords.
What the Exposed Database Contained:
The total size of the database was 477.95 GB and contained 1,507,301,521 (1.5 Billion) records.
There were a large number of remote and internal IP addresses, node names and other details that could provide a blueprint for internal functionality, logging, and overall structure of the network. Error logs, alerts, and job scheduling records that revealed cluster names, device names and many internal rules and tasks that were marked “Privileged =True”.
Read my full report on the Comcast Data Exposure here on WebsitePlanet