Religious website service Clover Sites exposed customer data for at least 6-7 months and the dataset was found twice on two separate databases.
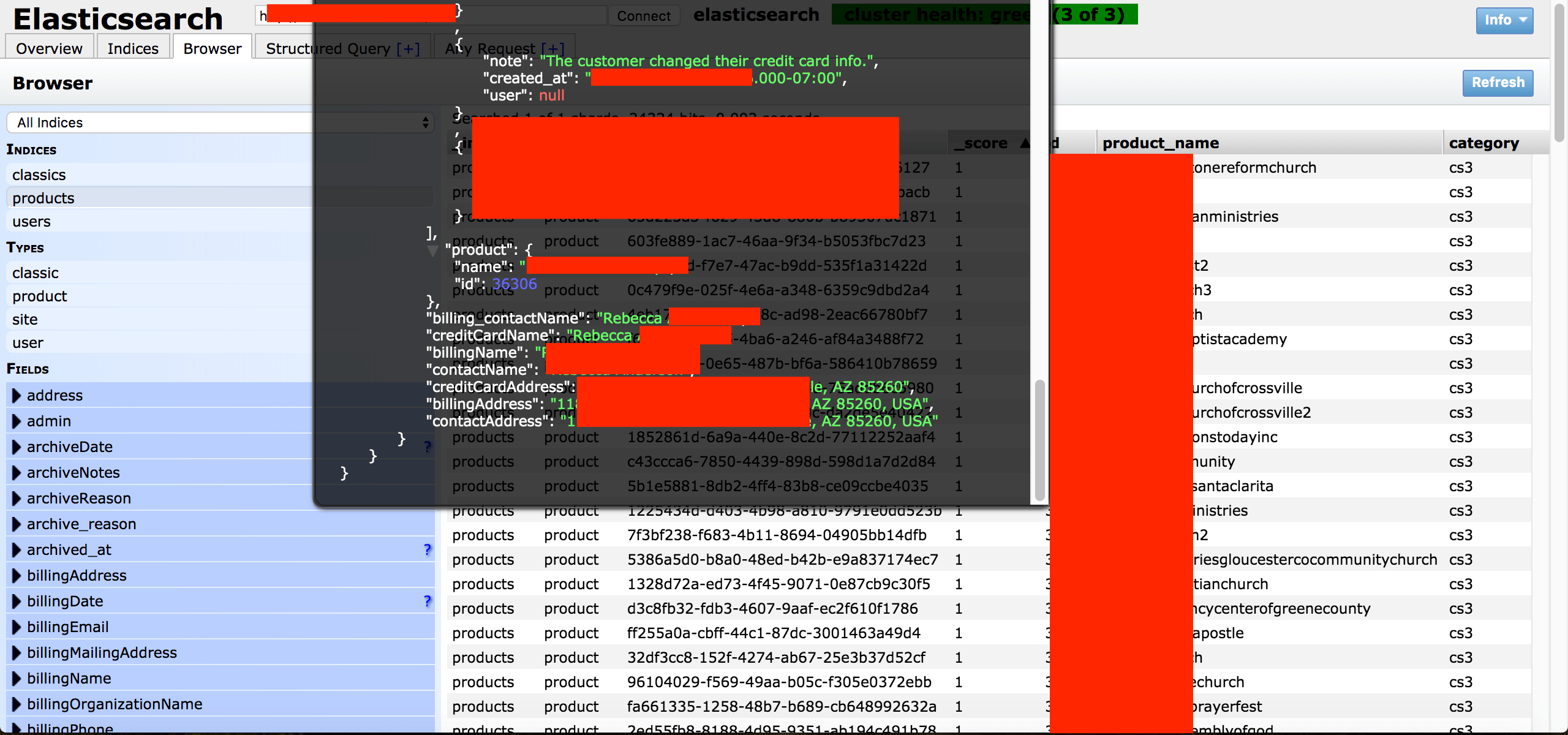
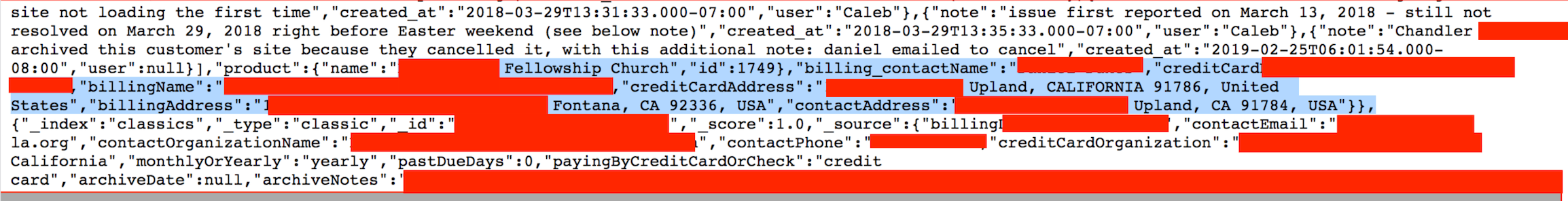
On May 22nd I discovered and reported a data exposure incident involving a religious website builder called “Clover Sites”. The non-password protected database contained 65,800 records and what appears to be all of Clover Site’s customer accounts past and present. The records were very detailed and included, customer names, billing info such as addresses and last 4 of credit card numbers. There were also detailed internal comments about calls, help requests, or if the customer was happy or unhappy.
“Clover Sites is a website creator that allows its clients to instantly create and manage websites and Clover Donations provides a simple way to accept donations online anytime and anywhere. It was created to give its users one of the best and front-end web presences available, combined with an un-intimidating content management system” According to their Crunchbase Profile
The following day on May 23rd, I noticed that the database was still publicly accessible and decided to call them by phone. To my surprise and shock the agent I spoke with told me “the manager would not speak with me and was aware of the situation that was already resolved”. The agent said that they were already notified by Bob Diachenko from Security Discovery roughly a month before my discovery.
At this point I assume there is a misunderstanding because I can see their customer files as I am talking with the agent. I ask again to speak with the manager and that I want to clarify the situation because the data is still open and again I get the same response. On May 24th I had a meeting with Bob Diachenko (who is Cyber Threat Intelligence Director here at Security Discovery). He discovered and reported the first data exposure incident to Clover Sites Inc. sometime in April about a month before I reported my own findings. He confirmed that he reached out to them and Clover Sites secured that database and then he never heard anything back from them.
We have determined that this was a second and separate data incident than what Bob Diachenko reported to Clover Sites in April. This would mean that Clover Sites’s full client data has been exposed online 2 separate times and was accessible to anyone with an internet connection. In early October I was finally able to get in contact with their parent company Ministry Brands LLC. On October 4th I received a thank you message from members of Ministry Brands confirming that they would take action. Within 24hrs public access was closed. Unlike the Clover Sites staff who ignored calls and emails, Ministry Brands acted fast and professionally to secure the data.
Irresponsible Disclosure
There were at least 1 or 2 other “researchers” who published this information while the database was still open. This is highly irresponsible to publish sensitive data while it is actively exposed and further jeopardize the already impacted individuals. There is a very important reason we did not disclose this discovery for 6 months. This is because we believe we have an ethical duty to those individuals who had their data exposed and not try to make news at the expense of innocent users and their data. True data protection is not a race to get your name in headlines, some free PR from your firm, or product. This approach goes against the hard work and countless hours of (often unpaid) research that is involved with the responsible disclosure process.
Here is what was discovered inside the database:
- The database set to open and visible in any browser (publicly accessible) and anyone could gain access to CloverSite Inc. data without administrative credentials.
- 65,800 records in total including user’s names, numbers, email, billing addresses, last 4 of credit cards. All in plain text.
- Internal records, customer email communication, other details about business processes or systems.
- IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper in to the network.
It is unclear how long the first database had been exposed or who may have accessed it. Based on the timeline we estimate that the customer data was potentially exposed from at least April-October (possibly longer). The most outrageous part of this data leak was the complete lack of response by members of the Clover Sites support team and management to 15-20 notifications and phone calls. This was the most blatant example I have ever seen of flat out ignoring multiple data exposure notices while still being aware of a previous data leak.
The danger of storing this type of information including the last 4 digits of a credit card and billing address is that it makes it extremely easy for cyber criminals to theoretically pose as employees and “verify” the rest of the card. This type of highly targeted phishing is a real risk because there is a relationship of trust with the customer and provider, so most people would not suspect anything if they received a call to update their payment method. This data set contained all of the necessary information anyone would need to potentially and successfully operate a phishing scam. With the detailed call notes the criminal could even say “I see that we last spoke on this date regarding this subject”. The fact that any member of the security community would publish this type of exposue before it was secured is the equivalent to providing cyber criminals with a treasure chest of potential victims.
“Ministry Brands, LLC has over 38 unique software platforms empowering over 115,000 churches and faith-based organizations in North America. These are critical tools ranging from church management platforms to financial accounting, website services, background checks, online donations, and many more” according to their website.
Clover Sites Inc. was founded in 2008 and is based in Newbury Park, California but was acquired by or partnered with Ministry Brands LLC. It is unclear if this data incident was reported to users who may have been affected or the State Attorney General’s Office. Despite several attempts and a request for comment regarding this data incident, Clover Sites Inc./ Ministry Brands LLC. has not responded or commented on the data incident at the time of this publication.