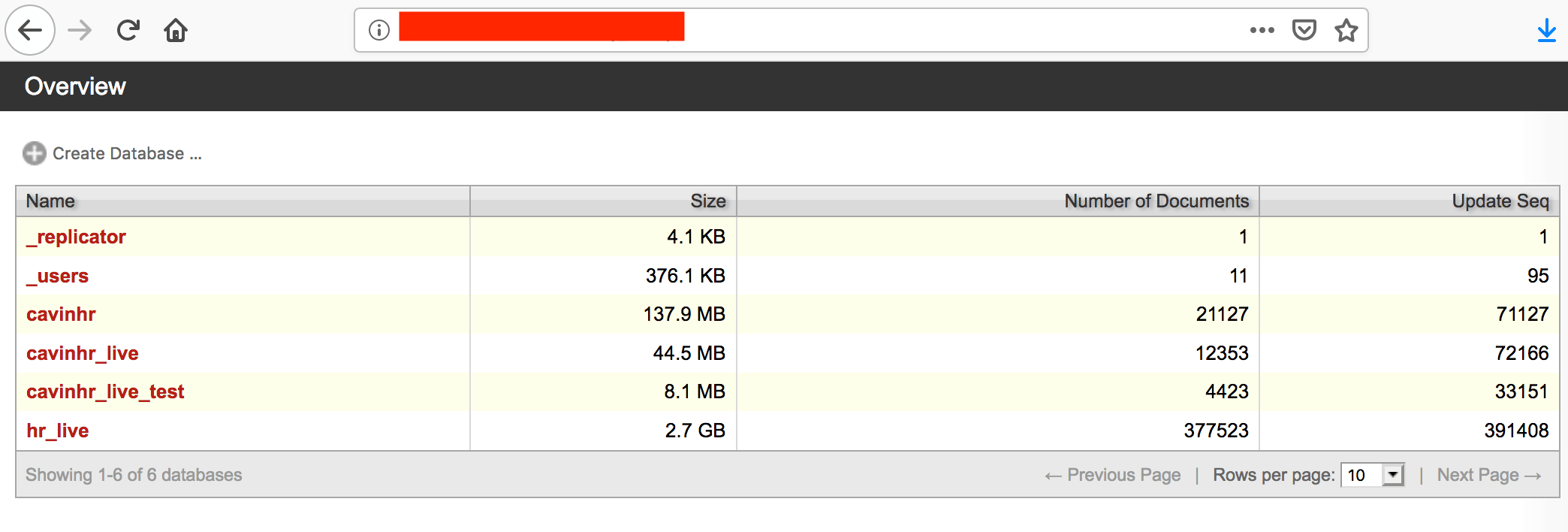
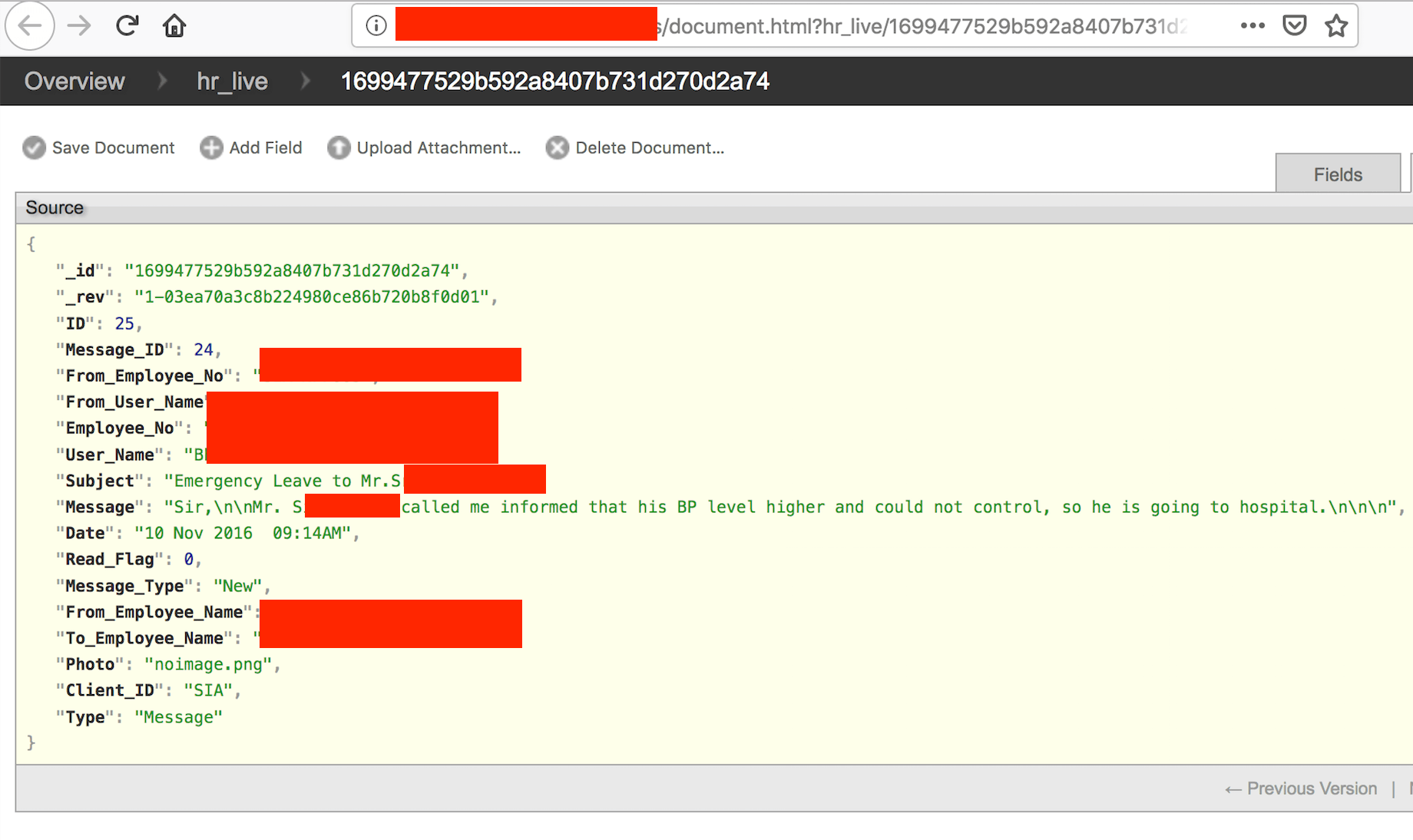
CavinHR had a data breach. Automation and technology is important to any business where time is money, but one thing to never overlook is cyber security. It is common knowledge in the business world that a company’s most valuable asset is their employees and their customers. You could imagine it would be a nightmare for any company to discover their employee data had been exposed online and non-password protected. Thousands of employee files were safely secured after researchers were able to notify CavinHR / Cavintek of a massive breach containing 411,061 files of internal and external client data.
Both Bob Diachenko and Jeremiah Fowler of Security Discovery had seen this database appear multiple times and had both reported it separately several months apart with no reply.
“We saw this particular database so often that we started to ignore it after sending several data breach notifications with no reply or response. We can verify that CavinHR / Cavintek was publicly accessible for several months and it is unknown how many other people accessed the database during that time”. – Jeremiah Fowler
Inside the database there were files that referenced Cavintek Inc that according to their website is registered in Miami, FL and CavinHR that has a California address, but nearly all of the internal files appear to show that the heart of the business or perhaps the entire operation is based in India? We should stress that there is nothing at all wrong with basing your business in India and there are many qualified IT professionals there. However, the problem comes with data security and protection laws. In India it could theoretically be hard to enforce data protection laws where in California and Florida there are strict regulations and a well established reporting process. There are also massive fines and penalties for failing to report data breaches to state governments and employees in a timely manner and in India this is still a gray area in terms of enforcement.
Companies should consider all options when using any software or service that stores their employee or customer data. This may include where is the legal jurisdiction is based in the event of legal liabilities of the employer or data management company. It does not hurt to ask the hard questions of your service provider and do as much research as you can before making a decision of who will have access to your organization’s most sensitive data.
Here is what we discovered that included the following:
- Type: CouchDb database open for public access, visible in any browser.
- Data could be downloaded, edited, or even deleted with no password or administrative credentials.
- 411,061 files of internal and external client data.
- 13,000+ Employee profiles some with names, date of birth, salary, bank info, religion, blood type and spouse data.
- Charity client data and detailed recipient information (PII).
- Other potentially sensitive data including EU citizen information with possible GDPR violations.
- Task information, employee ID numbers, emails (inbound/Outbound), notes including health information that is highly sensitive.
It seems that there are some precautions to prevent data from being intercepted, but once that data was backed up to their server it was open for anyone with an internet connection.
According to their website: “Our data centers are manned 24 X 7, with trained security guards, built-in firewalls and private subnets. Elaborate security policies control access levels for our own staff to access these servers. All databases are backed up every 5 minutes, so the maximum data loss is restricted to 5 minutes.
Best Practice – Don’t make it hard to contact you
Email security is great, until it’s not. We always include the exposed IP address URL and screenshots of what we found in the data breach notification. CavinHr/ Cavintek had enabled a security feature that bounced every email with an attachment or link to spam classification. Don’t make it hard to report issues, bugs, or a data leak and then when something happens it is nearly impossible to notify your organization. Companies should make it easy and even include a simple text document in their database with instructions of your disclosure reporting protocol. This way if a legitimate security researcher finds your database you can rest assured knowing they will contact you fast to help you close the data exposure and not spend days or weeks sending emails off in to space while your data is at risk. Then, obviously don’t ignore data breach notification emails.
*We have asked to speak with someone at CavinHr/ Cavintek to answer any questions of how we discovered the database. Despite multiple requests for comment, no one has replied at the time of publication.