Kool King Shop, (https://www.koolkingshop.fr/), a French-only online shop for kids who purchased Burger King’s menus, had customers data exposed in a misconfigured database.
An open and unprotected Elasticsearch cluster with plain-text data was left unattended at least since April 24, 2019, according to Shodan historical data.
Among exposed data:
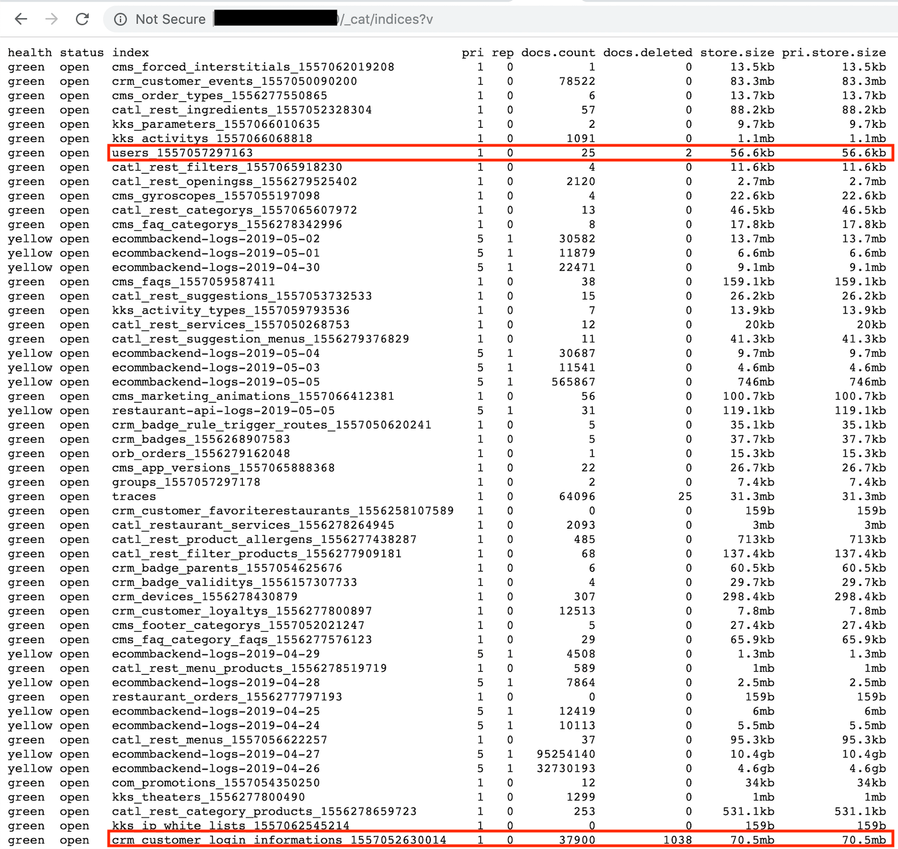
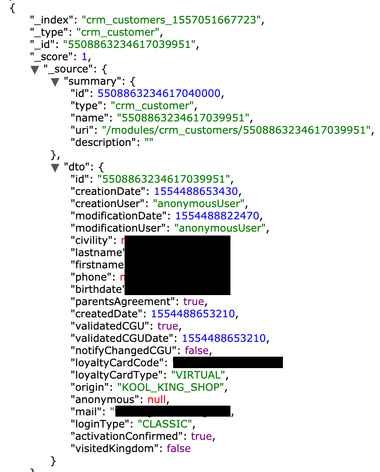
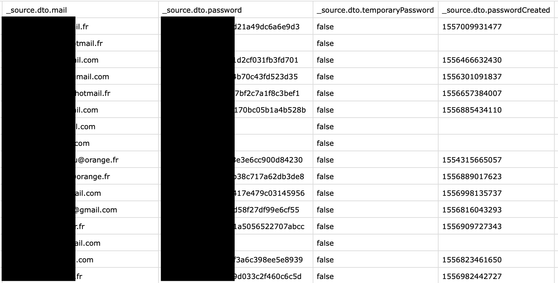
- 37,900 records with details such as: emails, passwords (access to the portal), names, phones, DOB, voucher codes, links to the externally stored certificates etc.
- 25 administrator CRM access details (Burger King stuff), with names, emails, encrypted passwords
- Ecommerce CRM backend logs, with internal details and debug information
I have immediately sent a security alert to the database administrators (whose emails were listed as well) and public access was disabled. Burger King team provided me with the following statement:
We would like to thank you for your responsible disclosure of a possible security vulnerability in our infrastructure on certain customers’ data.
Data protection is critical to Burger King and we do take these matters very seriously. All the necessary actions legally required have been taken internally and with our service provider immediately after this incident came to our knowledge to ensure the effective resolution of the problem as well as the safety of our clients’ data. We are also liaising with the relevant national authority having jurisdiction in this respect.
We wanted to keep you informed that the issue has been investigated and that such possible vulnerability is now corrected.
Danger of having exposed Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.