On July 5th I discovered two (!) open and publicly accessible MongoDB instances which appeared to be part of the GootKit network – one of the most advanced banking Trojans discovered in the wild in the summer of 2014.
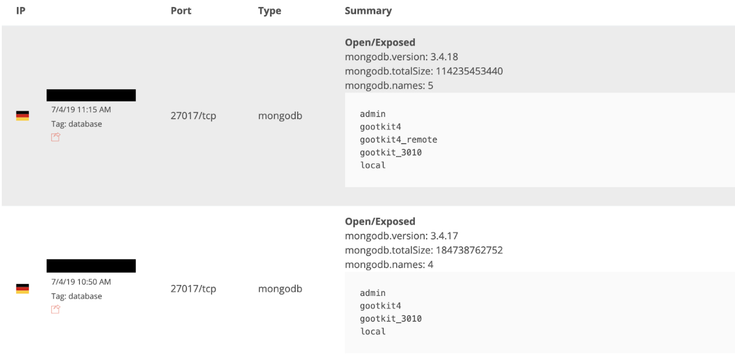
Both instances were indexed by public search engines, here is how the banner looked on BinaryEdge:
The databases were taken down on July 10th.
You can read more about GootKit capabilities as researched here.
In short, it is a very capable and intrusive malware used in online banking fraud attacks that target consumer and business bank accounts primarily located in Europe. Once infected, the computer sends the stolen data to a bot command and control (C&C) server, where the data is stored and processed. Analysis of the databases content confirmed this – all the infected machines were located in Europe with the top countries being Poland, France, United Kingdom, Italy, Bulgaria.
Here is the short summary of the information that was left exposed. This also shed some light on the nature and origin of the data. Please note that this is not a detailed analysis but rather an overview of the incident. My primary goal is to raise awareness and hope that my discovery serves as a wake up call for the financial industry, users, and info sec community.
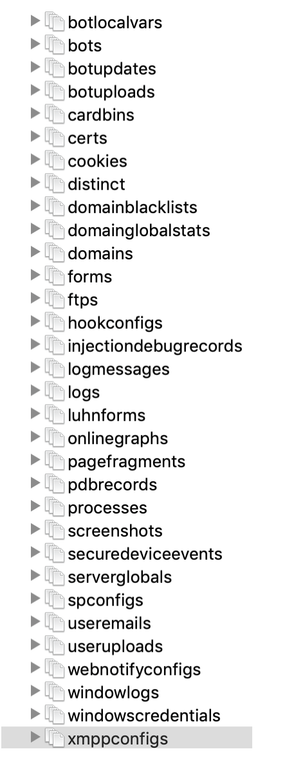
GootKit4 database contained 32 collections:
Not all collections contained data. The most valuable information was in the “Forms” folder. This is where the scraped data that the users were filling in while working on an infected machine was stored: plain text passwords, configuration details, bank accounts, mail accounts logins, online shops, credit card details etc – everything where a password was needed was collected and stored.
In total, we estimate the following amount of information was compromised:
- 1,444,375 email accounts
- 2,196,840 passwords and configuration pairs: online shops, emails, banking applications, streaming and other online services, internal network passwords, and many more.
- 752,645 usernames
In addition to personal and sensitive data collected from the infected machines the database also contained several folders with configuration details which might be of interest for malware researchers and law enforcement authorities.
You can read more details on this case here:
***
As we see a never-ending loop of these incidents, we at SecurityDiscovery.com have decided to offer a live educational sessions (webinar or offline workshop) for raising cyber security awareness within your organization, to prevent potential issues in the future. We use real world examples and promote that data security is important to every employee and at every level inside the organization.
It can be an online webinar session (estimated 1h long), with Q&A session or an offline meeting in your offices, live interaction with your team (master class included).
Proposed content includes:
- Description of tools and techniques we use to identify vulnerabilities, PII and sensitive data online: no hacking, just google-it.
- How to ensure your data / your company’s data is not exposed to the public internet, security tips from professionals
- Recommendations and best practice on main noSQL databases configurations and maintenance (MongoDB, CouchDB, Elasticsearch)
- Case studies: analyzing related data appearance online
- Live search for data and master class
Please feel free to send your requests to alert(at)securitydiscovery.com or bob(at)securitydiscovery.com
Let’s educate your team!