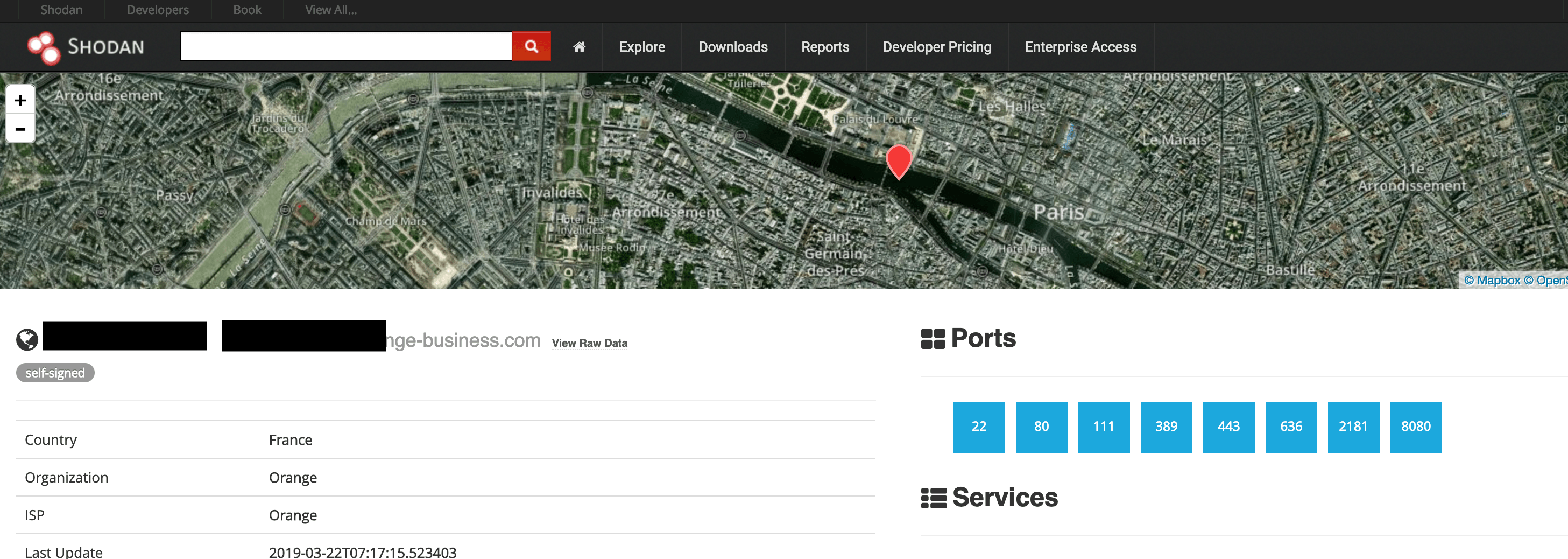
On March 21, 2019, I have discovered a publicly available service instance which appeared to contain credentials and login details to Auchan E-Commerce infrastructure.
IP with Marathon and Zookeeper instances was indexed by public search engine Shodan and was open for public access, no login or password needed to access.
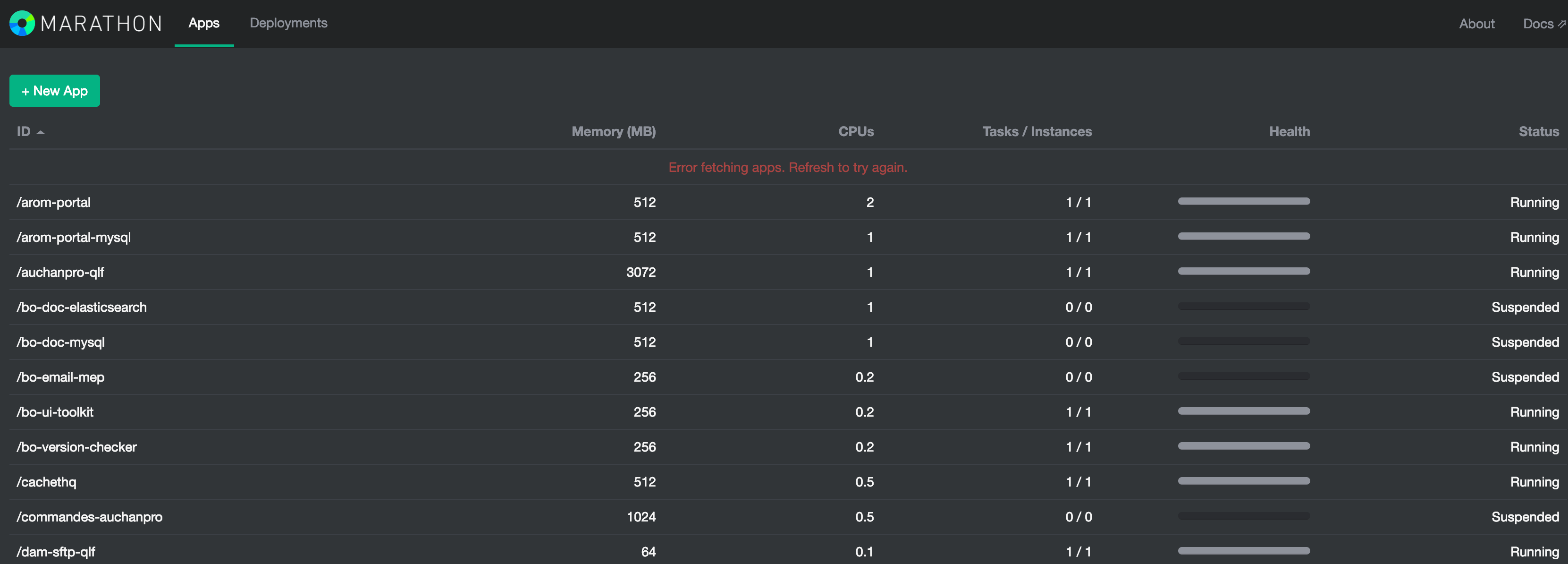
Marathon is a container orchestration platform for Apache Mesos and is used for manage and schedule resources. It allows you to monitor and operate applications and frameworks within a single container and configure them according to their health status. Typically, you can define fine-grained access to applications by creating advanced ACL (access control list) groups in your native Marathon instance, however, in this case platform GUI was accessible without any authorization:
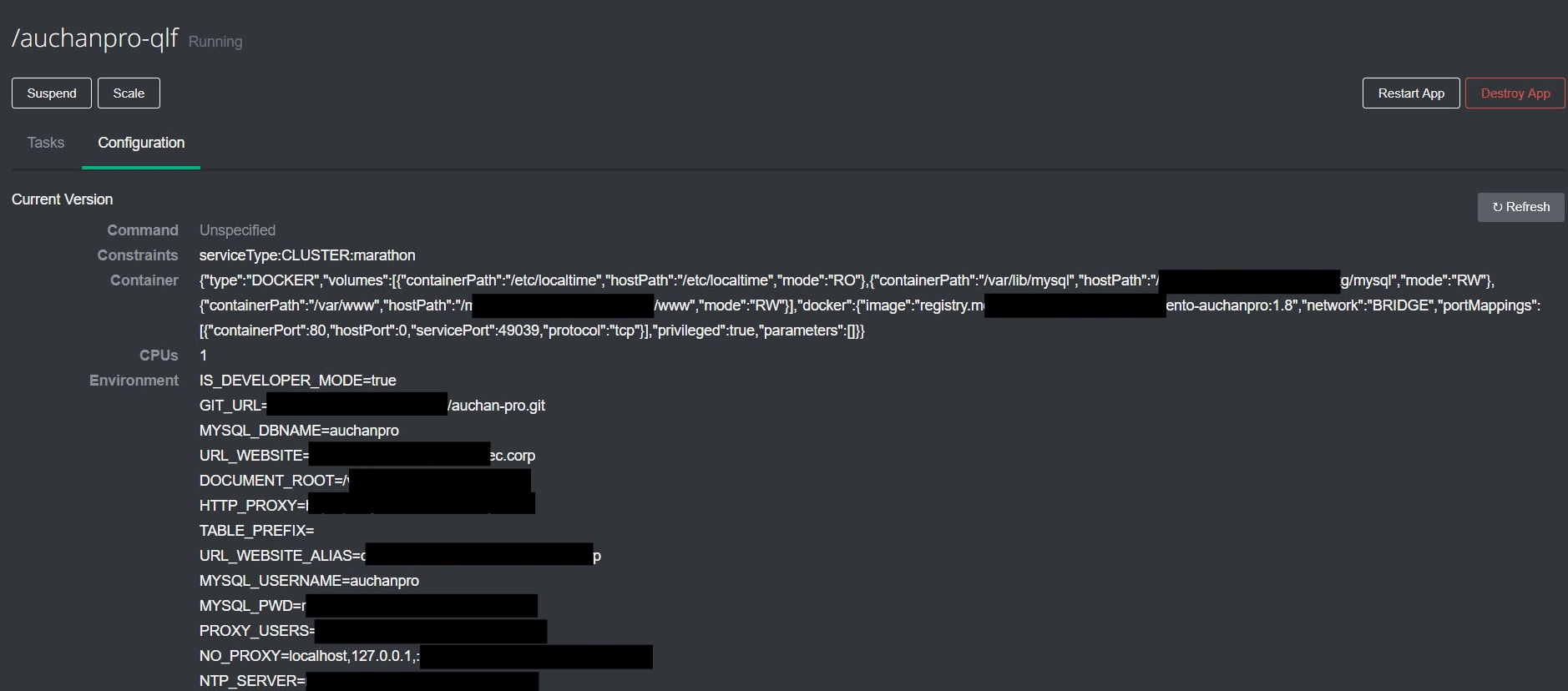
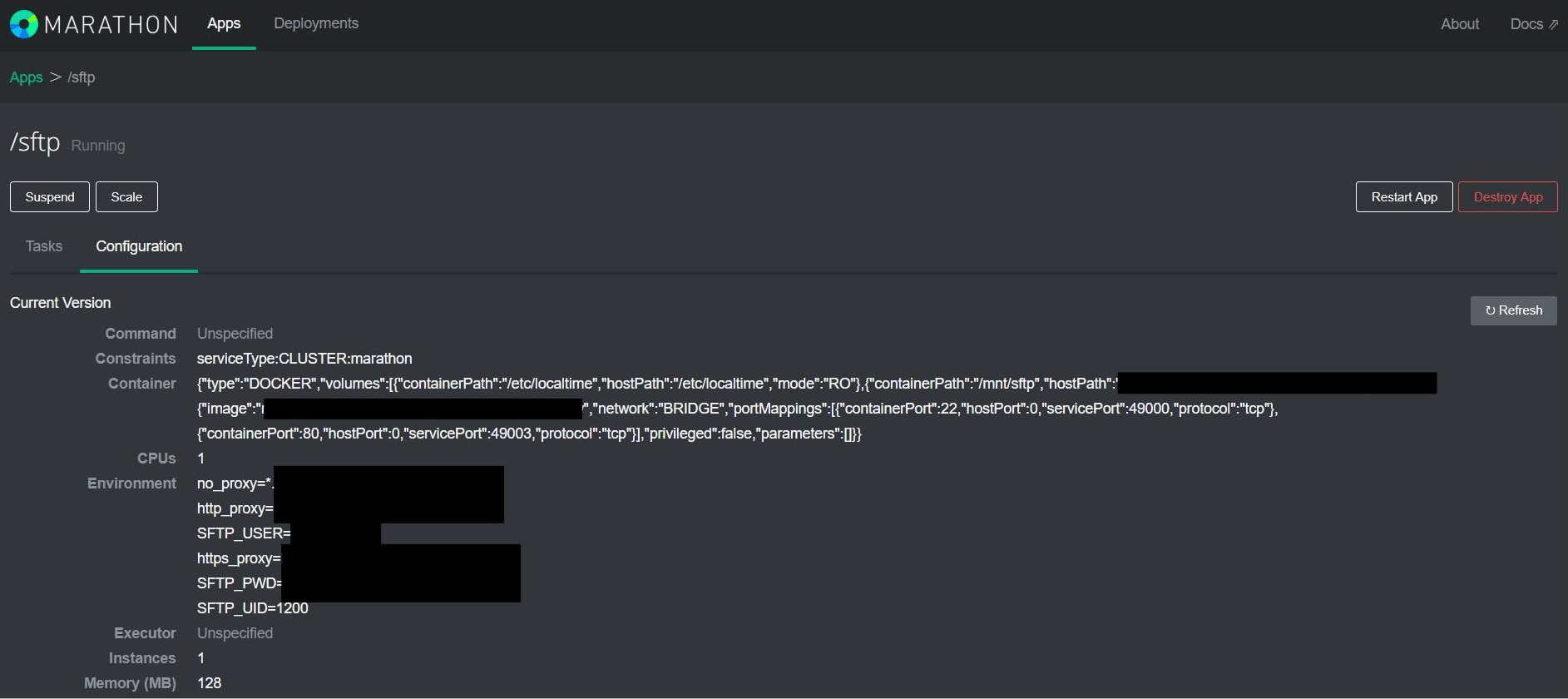
Configuration details (plain text password and logins) were left wide open:
More than a dozen of other databases and environments (mySQL, SFTP, SSH private keys, Elasticsearch, Redis etc) configuration details were left open unattended.
Additionally, a Zookeeper instance on port 2181 was also misconfigured and publicly available.
According to Shodan’s historical data, port 8080 for this IP has been configured for public access since Feb 13, 2019.
I have immediately sent an alert to Auchan, however, the response was only received more than 48 hours later, when I asked my Twitter followers to help to reach out to the responsible persons. Thanks to the assistance of Damien Bancal from zataz.com.
A representative of Auchan IT department said in an email that it was “a non production platform and “no users/customers datas, privacy issues or production compromise are involved”.
According to a representative, misconfiguration was quickly removed and all the passwords revoked.
It is important to highlight that we at SecurityDiscovery follow strict white-hat protocol and do not check the passwords against compromised systems, so we cannot confirm or deny whether production systems were at risk or was it a non-prod environment.
In any case, it is, of course, not acceptable for any organization or company to have plain-text passwords exposed in public internet.
We will update this article if/when more details become available.