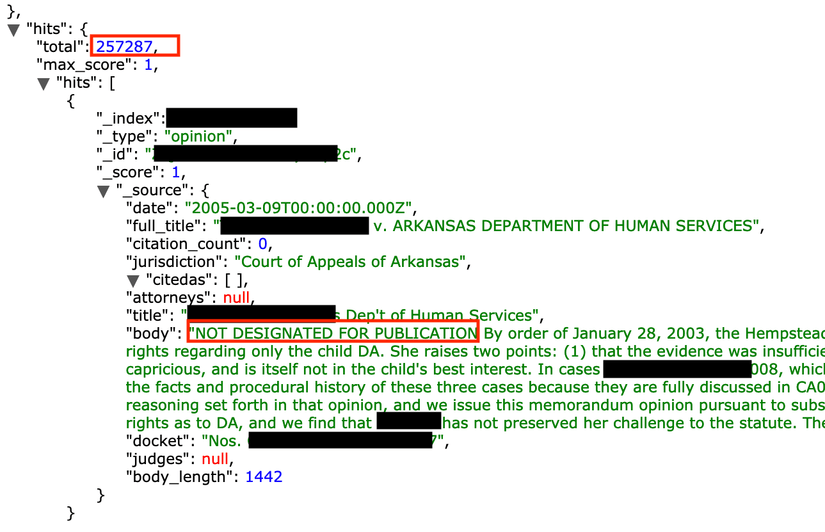
On March 2nd, 2019, I have discovered an open and unprotected Elasticsearch cluster which contained 257,287 legal documents labeled as ‘not designated for publication‘. The research was part of our initiative to identify and alert organizations that are misconfiguring noSql databases, such as MongoDB, CouchDB, Elasticsearch etc.
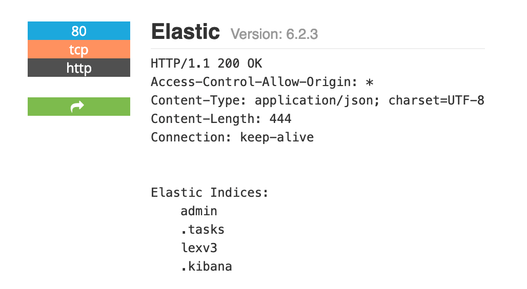
A 4.7GB instance hosted on a US-based Amazon AWS server was indexed by popular IoT search engines, such as Shodan:
After initial investigation we assumed that data is managed by Lex Machina, an IP litigation research company and division of LexisNexis that develops legal analytics data and software, and sent them a security notification alert. No response was received and after almost two weeks database was secured and is now not reachable.
However, upon a closer look at the cluster’s digital footprint, I tend to assume that database in question was handled by a company named LexSphere (based in India) which provides legal outsourcing services to a law firm called LexVisio.
Still, no official confirmation on either version is received, more than 250K sensitive documents were freely available for anybody who know where to look.
Danger of having exposed Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
About author and security researcher:
Bob Diachenko has over 12 years experience working in corporate/product/internal communications with a strong focus on infosecurity, IT and technology. In the past Bob has worked with top tier media, government agencies, and law enforcement to help secure exposed data. Follow Bob on Twitter and his blog on Linkedin,
Email: [email protected]