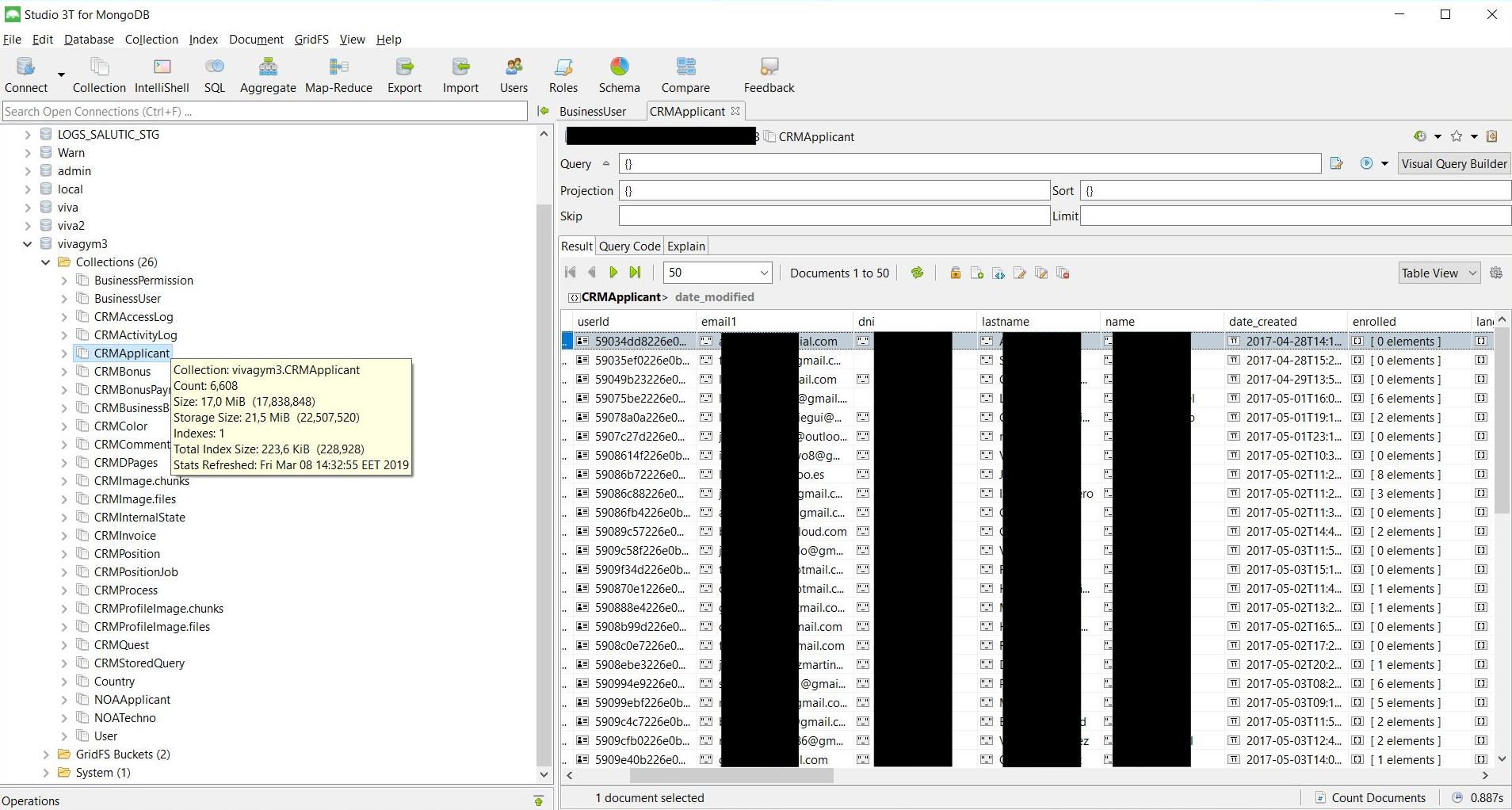
On March 8th, 2019, I have identified a passwordless MongoDB database that was exposing sensitive information of an estimated 6,608 VivaGym job candidates and other business related data. VivaGym is a Spanish low-cost gym franchise operating in Spain and Portugal.
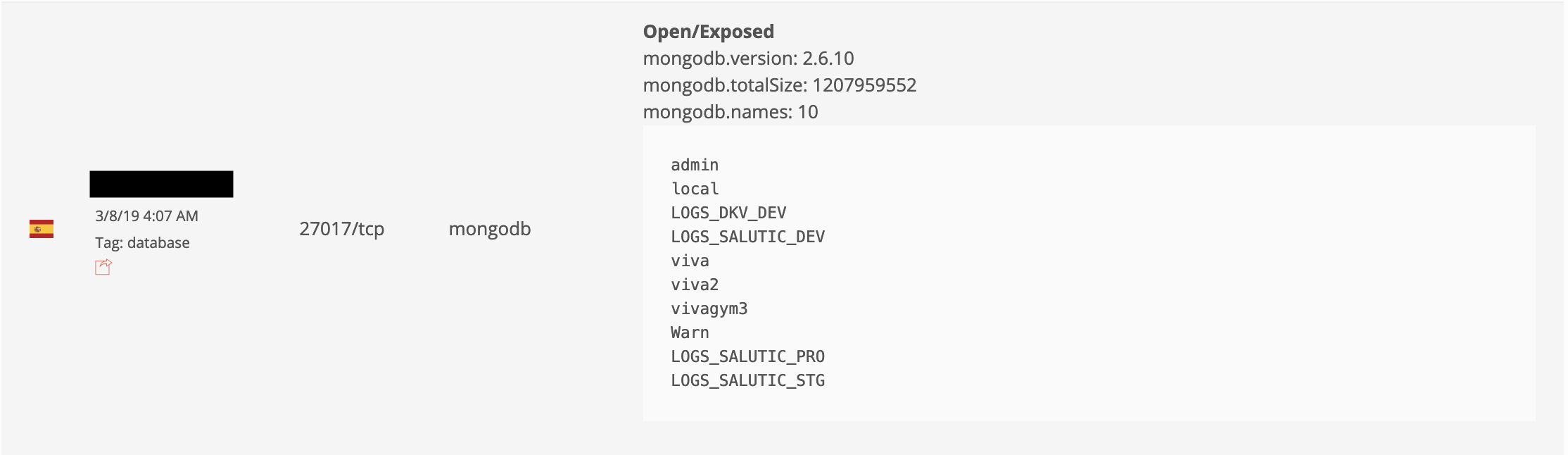
Database was freely accessible and indexed by public IoT search engines, such as BinaryEdge. See the screenshot below:
At the moment of the discovery, database already had a ‘WARN’ collection, this is evidence that it had been accessed by malicious script which targets unprotected databases and then removes its content and puts a Bitcoin ransom note inside the database. You can read more insights on this type of attacks here.
The misconfigured MongoDB in question was part of VivaGym’s recruitment website infrastructure and managed by one of their technological partners. The information exposed included the following user data:
- Encrypted password
- DNI
- Last name / first name
- Username
- Login date and time
Additionally, similar information on 74 “Business Users” was also available for access, plus technical logs for the system.
The database was secured within hours after I notified VivaGym via email and pubic access was restricted on the same day of discovery, March 8th.
A representative of VivaGym confirmed that “supplier corrected the issue immediately after it was raised with them and that a new process is in place to ensure there is no recurrence“.
According to the representative, VivaGym had informed the Data Protection Authorities (even though the issue was below the required threshold) and they will also inform all users who were affected. Details of Viva Gym members were not included in this database.
The danger of having exposed an MongoDB or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers and it is a serious threat. The public configuration allows the possibility of cybercriminals to manage the entire system with full administrative privileges. Once the malware is in place, criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains. It is unclear who else may have had access to the database, but the discovery of the ransomware note is proof that it was compromised before I was able to responsibly disclose the discovery.