Sometimes databases are left wide open not only by legit companies, but misconfigured by malicious actors themselves.
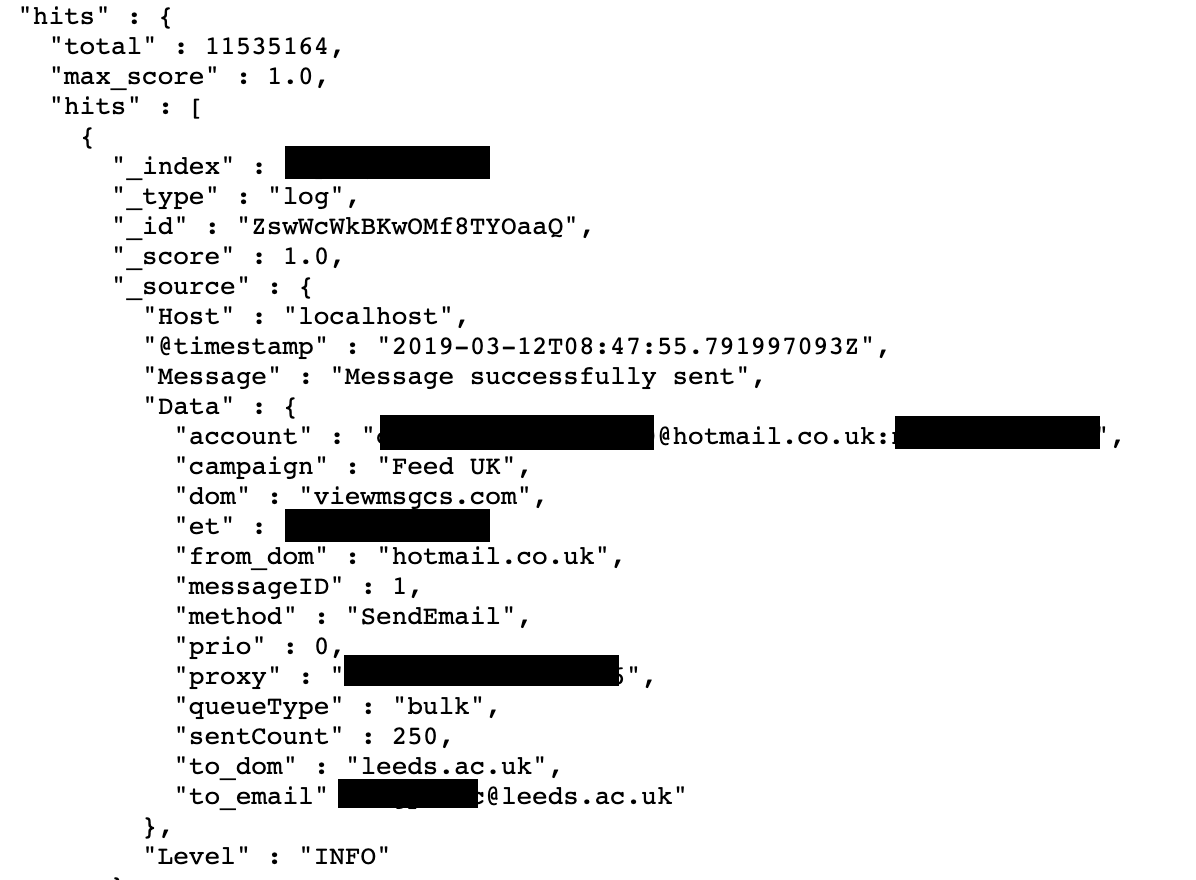
Last month I have discovered a publicly available database with almost 5GB of 11,535,164 records with compromised emails and plain-text passwords, exposing the entire operation of one of the spam operations targeting UK-based users.
The structure of the records left almost no doubts on the malicious nature of the dataset:
IP with database was hosted on a domain called ‘mail.intelimost.com‘ which is blacklisted by Spamhaus – an international nonprofit organization that tracks spam and related cyber threats.
Same domain is mentioned in a discussion on the Bleeping Computer’s forum. One of the forum’s users confirmed my theory:
A bot or the attacker use credential stuffing against mail domains with a combo of usernames and common passwords. Once they get a strike on that then they read the last mail items using IMAP, reply using authenticated SMTP and then phish for more credentials, They then use these captured credentials to do more IMAP reading, send more emails.
So, in a layman’s term: there had to be just one “patient zero”with a password leaked in one of many previously (un)reported leaks (like Collection 1 or Combos of any kind), to start the whole avalanche-like operation.
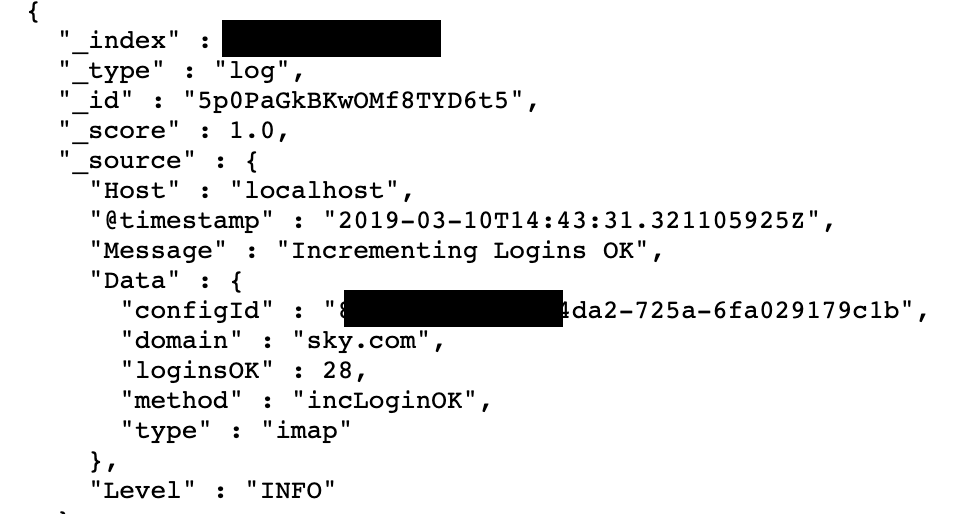
IP with database had also a dozen of open ports, one of which being responsible for a Kibana, user friendly interface for Elasticsearch databases.
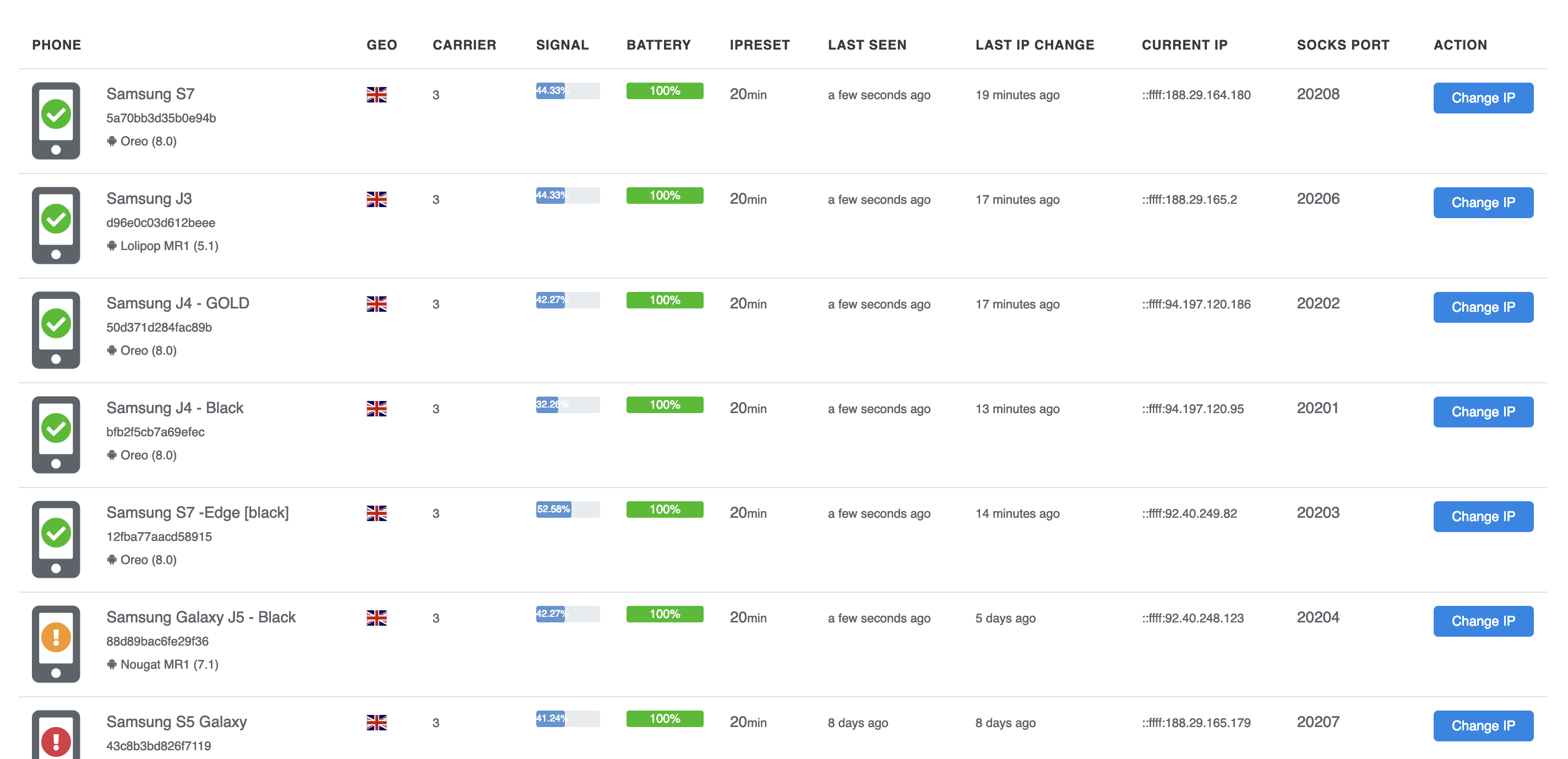
Additionally, a proxy server with several connected cell phones was also part of spammer infrastructure:
Interestingly, spam operations log covers ten days period from March 8 to 18, with a specific UK target. Spammers used two types of campaigns:
- Boost UK
- Feed UK
Shortly after discovering the malicious database I got in touch with Zack Whittaker of TechCrunch with whom I have worked in the past on a number of similar investigations. Zack was able to analyze the data with me and connect to a hosting company to shut down the IP with database.
You can read his brilliant analysis on TechCrunch.
On a related note, we have provided a copy of the database to Troy Hunt. Anyone can now check breach notification site Have I Been Pwned to see if their email was misused.
This case reminds me on several other occasions I reported at some points in the past – when malicious actors create a sophisticated system of proxying and logging, leaving so much tracks to identify their patterns for authorities in the investigations to come. At the same time, it shows us – again! – how important a proper cyber hygiene should be. It only takes one non careful click to have all your email and personal data compromised!