SMS marketing has been an increasing problem with the rise of scripts and applications and that send literally countless messages as fast as they can be sent.
On April 11th, I discovered an open and unprotected MongoDB instance named ApexSMS indexed by many public search engines, e.g. BinaryEdge:
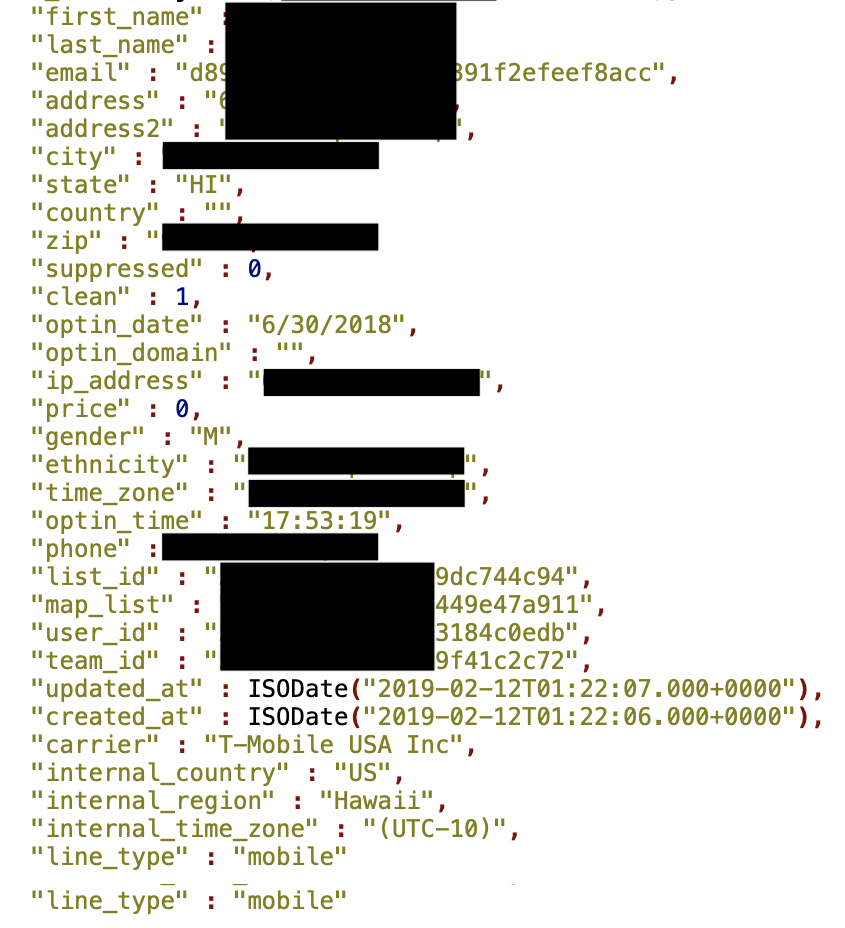
This database contained a massive amount of data related to an SMS operation center with one of the most prominent folder called “leads” that had 80,055,125 records, including:
- MD5 hashed email
- First/last name
- City/state/country/zip
- IP address
- Phone number
- Carrier network for mobile
- Line type (mobile or landline)
Upon further research it was identified that the MongoDB instance name ApexSMS is also the name of a SMS Bombing program with the same name that is highly advertised on hacker or black hat forums. What is SMS Bombing? Cellular phones use SMS, to send text messages. Typically, cellphone users send one message at a time. However, an SMS bomber is a software program that duplicates the same message multiple times or rotates different messages and sends all the messages to a number of your choice. This can be used for pranks, harassment, or in this case marketing products or services.
It appears that the alleged owners of this database might have an official cover as mobiledrip.com, however, this is still to be confirmed as we never heard back from anybody at MobileDrip.
According to the website, “MobileDrip is a cloud based sms platform that’s optimized for high volume messaging with all the tracking, automation, segmentation, and data management features you need to maximize the profitability of your campaigns”. They also claim on their website that they do not engage in spam.
MobileDrip’s website also gives a clear description of how the automated SMS marketing works:
- Attach drip campaigns to your lists and list segments to completely automate your sending.
- Drip campaigns include the same features as broadcasting
- Rotating Providers, Rotating Messages
- Auto-replacing Domains
- Segmenting data by carrier, gender, ethnicity, and location so you can optimize the messages you’re sending based on the leads
- View stats for each message inside the drip campaigns
- View drip message queue and history with stats on all messages.
Database also contained the messages sent to millions of people and these messages were designed to trick people into clicking links by pretending to be a referral from a friend or family member. The script also tracked responses or actions. In one exchange the person receiving the SMS replied “Nathan is married and didn’t talk to you yesterday because I his wife had this phone. Text this phone I’ll have you charged with harassment”.
It is unclear how long this MongoDB instance was accessible who else may have had access to the millions of contacts. Database was quietly secured several days after the initial find.
This does raise the issue once again that data security can affect legitimate businesses and what many would consider “gray marketing” at best. At the end of the day these services are still using and improperly storing the information or data of millions of people.
Zack Whittaker of TechCrunch had a closer look and investigated more on this case, you can read his take here.